Cyber threats are constantly evolving, and it is crucial for organizations to stay ahead of potential attackers. And this is where auditing cybersecurity and cybersecurity audit techniques and tools come into play.
Here we'll look at what cybersecurity audits are for assessing an organization's security posture. We will also look extensively at cybersecurity auditing objectives and the resulting types and methods used by cybersecurity auditors, giving you a deeper understanding of the importance of regular audits. And, of course, we'll detail look at cybersecurity auditing techniques and tools that help significantly reduce its complexity and cost, increase its effectiveness, and even automate it in many ways.
So, if you are a business owner, IT professional, or just interested in cybersecurity auditing, this article will provide you with valuable insights and deep knowledge.
What is a cybersecurity audit?
A cybersecurity audit is a comprehensive set of activities and techniques to evaluate a company's security, architecture, infrastructure, or other information systems. This involves evaluating a company's security posture by identifying potential vulnerabilities and threats and assessing its compliance with industry regulations and best-world practices. Regular cybersecurity audits help ensure that systems are secure and protected against new potential cyberattacks and help identify new areas for improvement to enhance a company's overall security state.
Cybersecurity audit types
Audit in cybersecurity can be divided into a few types, and organizations need to choose the right type of audit based on their unique security needs and requirements. Here we will explore some common types of cybersecurity audits in more detail.
New audit
This type of audit ensures that the security measures of the new project are profound and meet the required standards. New audits typically involve a comprehensive review of the project's security measures, from system architecture and access controls to data encryption and incident response planning.
Repeat audit
A repeat audit is conducted for a new version of an existing project being revised with new or fixed features. This type of audit aims to assess the effectiveness of the updated security measures. Repeat audits typically involve reviewing the changes made to the project since the previous audit, focusing on the areas where vulnerabilities were identified.
Fix audit
A fix audit is conducted to review the fixes made to the findings from a current or prior audit. This audit aims to ensure that the identified vulnerabilities have been profoundly addressed. Fix audits typically involve a targeted review of the areas where vulnerabilities were identified, focusing on verifying that the appropriate fixes have been implemented and are effective.
Retainer audit
A retainer audit is conducted to review project updates constantly. This type of audit ensures that security measures are updated regularly to keep pace with evolving threats. Retainer audits typically involve ongoing monitoring of the project's security measures, focusing on identifying and addressing new vulnerabilities as they are discovered.
Incident audit
An incident audit reviews an exploit incident and the root causing the incident identifies the underlying vulnerabilities and proposes fixes. This type of audit helps organizations understand and take appropriate action to prevent similar incidents from happening again. Incident audits typically involve a comprehensive review of the incident, including a technical analysis of the exploit and the vulnerabilities that allowed it to occur and an assessment of the organization's incident response processes and procedures.
Cybersecurity audit goal
Also, in addition to the general state of your project and the corresponding type of audit, there are other key and precise differences, such as the goals of the audit, which directly affects the choice of area, methods, and tools to conduct it.
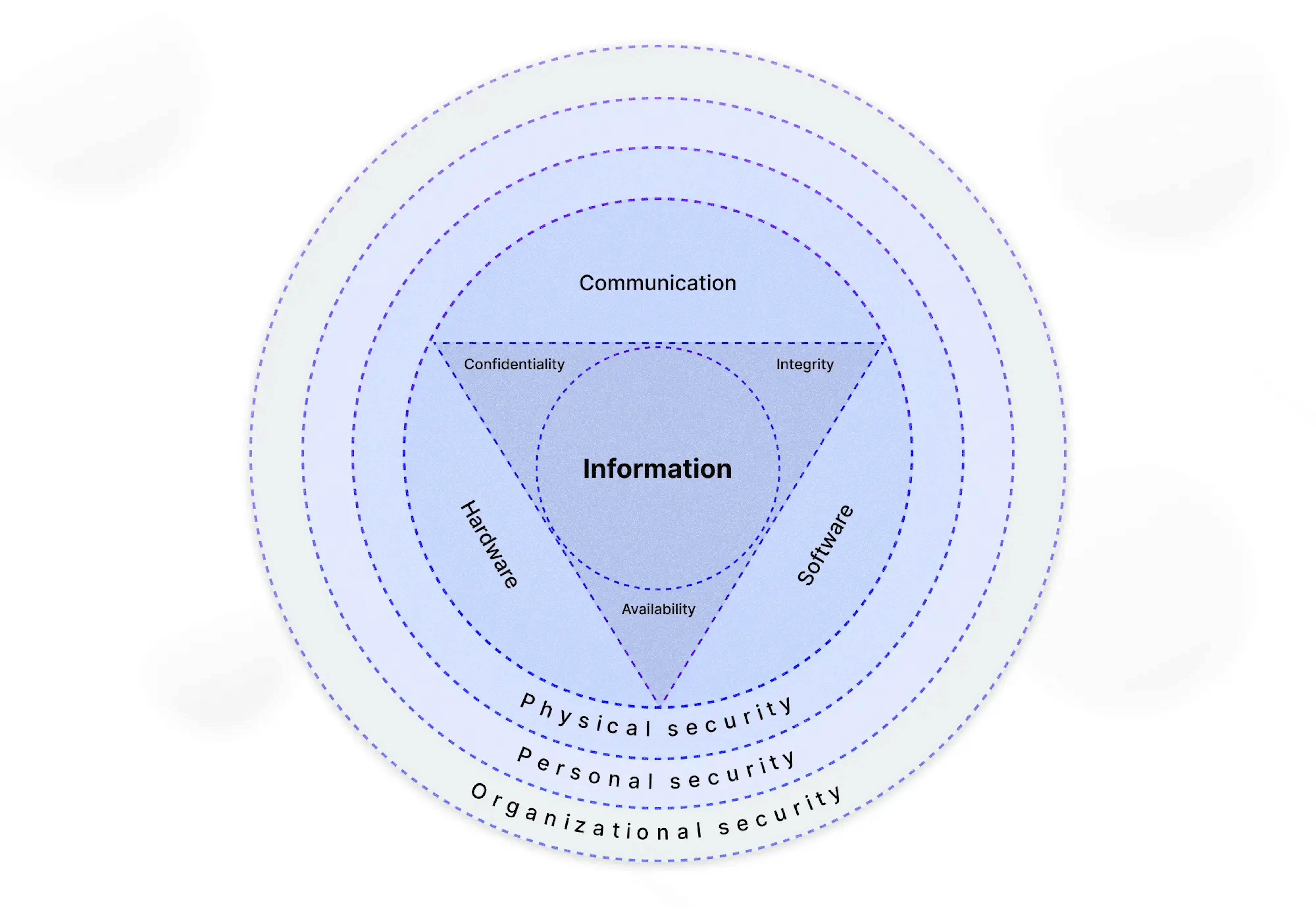
Generally, you can divide any audit into two groups: goal and non-goal.
The Audit Goal is to examine the entire code base and project documentation to alert the project team, usually before launch, to potential security issues that must be addressed to improve the security posture, reduce the attack surface, and mitigate the consequences.
The Audit Non-goal is not limited to checking the code base since any code base cannot be completely perfect. Instead, a non-goal audit is usually conducted after a company and product launch and represents the best efforts of trained security experts working at all levels at once, within reasonable limits and established agreements, of course.
Cybersecurity audit areas
Different security objectives can affect which areas of an organization's security measures are audited. Common areas of focus for cybersecurity audits we will describe below.
Auditing information and documentation security
Auditing information security involves reviewing an organization's information and documentation management processes and assessing the security of sensitive information. Auditors may examine how data is classified, handled, and stored and examine the policies around access control, authentication, and data encryption. This audit can also include analyzing the document retention policy, the regularity of backups, and the access logs that show who accessed what information and when.
Auditing company infrastructure
Auditing Company Infrastructure involves reviewing an organization's IT infrastructure and assessing its security posture. Auditors may examine the security of servers, firewalls, switches, routers, and other networking components, as well as the security of data centers and cloud-based infrastructure. It may also include evaluating security monitoring processes, backup and disaster recovery processes, and access control processes.
Auditing solution architecture security
Auditing solution architecture security involves reviewing an organization's software solutions and assessing the security of the architecture. Auditors may examine the security of application design and development practices, including vulnerability management and code reviews. It can also include an analysis of access controls in the application, authentication and authorization mechanisms, input validation, and output sanitization.
Auditing processes and practices
Auditing Processes and Practices involve reviewing an organization's internal processes and practices and assessing their impact on security. Auditors may examine the organization's change management practices, incident response procedures, and security awareness training programs. It can include an analysis of the effectiveness of the processes and practices in mitigating security risks and improving overall security posture.
Auditing services and tools
Auditing Services and Tools involve reviewing an organization's third-party services and tools and assessing their impact on security. Auditors may examine the security of cloud-based services, virtual private networks, and other security-related services. It can also include an analysis of the vendor management process, the documentation of service-level agreements, and the implementation of secure connection protocols.
Auditing suppliers and supply chains
Auditing Suppliers and Supply Chains involve reviewing an organization's suppliers and their impact on security. Auditors may examine the security of the suppliers' systems, processes, and practices and their compliance with industry regulations. It includes an analysis of the due diligence processes for selecting suppliers and maintaining supplier chains.
Auditing employee access
Auditing Employee Access involves reviewing an organization's employee access and assessing the risk of insider threats. Auditors may examine the organization's access control policies and how employees are trained to handle sensitive information and prevent accidental or intentional data breaches. It can also include an analysis of the implementation of least privilege and separation of duties, the documentation of role-based access controls, and monitoring access logs and failed login attempts.
Audit findings classification
The vulnerabilities found during the audit are typically classified into different categories, which helps to understand the nature of the vulnerability, potential impact/severity, impacted project components/functionality, and exploit scenarios. Trail of Bits, for example, uses the below classification:
- Access controls. Authorization of users and assessment of rights.
- Auditing and logging. Auditing of actions or logging problems.
- Authentication. Identification of users.
- Configuration. Security configurations of servers, devices, or software.
- Cryptography. Protecting the privacy or integrity of data.
- Data exposure. Unintended exposure of sensitive information.
- Data validation. Improper reliance on the structure or values of data.
- Denial of service. Causing system failure.
- Error reporting. Reporting of error conditions in a secure fashion.
- Patching. Keeping software up to date.
- Session management. Identification of authenticated users.
- Timing. Conditions, locking, or order of operations.
- Undefined behavior. Behavior triggered by the program.
Technics of cybersecurity audit

Of course, looking at so many features of the audit, it is obvious that, depending on them, there are many techniques for their conduct. Many automatic analyses are performed with tools, and some require manual assistance. Let's take a closer look at their cybersecurity audit techniques.
Manual specification analysis
Analyzing the specifications of a project describes in detail what (and sometimes why) the project and its various components are supposed to do functionally as part of their design and architecture. From a security perspective, it specifies the data and its place, who can access what and when, trust relationships, threat models, potential attack vectors, scenarios, and mitigations.
By analyzing the specification, auditors can gain valuable insights into the design and architecture of the project and identify potential security risks and vulnerabilities. This analysis allows auditors to evaluate the assumptions made and indicate any shortcomings in the security measures that have been put in place.
Manual review of documentation
Documentation typically takes the form of Readme files in the Github repository, describing individual solution functionality combined with individual code comments. Documentation often serves as a substitute for specification and provides critical insights into the project team's assumptions, requirements, and goals.
Understanding the documentation before looking at the code helps auditors save time inferring the project's architecture, solution interactions, program constraints, data flow, etc. Mismatches between the documentation and the code could indicate stale/poor documentation, software defects, or security vulnerabilities.
Auditors must encourage the project team to document so that they do not need to waste their time inferring details from the code.
Automating testing
Testing is a fundamental software engineering practice used to determine if software produces expected outputs when executed with different chosen inputs. And in a cybersecurity audit, automated testing is a critical technique for validating the security of a software project.
Test coverage and test cases provide valuable insights to auditors into assumptions and edge cases for vulnerability assessments and indicate project maturity. So auditors should expect high testing and test coverage, as this is a must-have software engineering discipline.
As the famous quote by E.W. Dijkstra says, "Program testing can be used to show the presence of bugs, but never to show their absence!"
Automated static analysis
In a cybersecurity audit, static analysis is a technique for analyzing program properties without actually executing the program. This contrasts software testing, where programs are executed/run with different inputs. So static analysis can be performed on any type of software project. Tools can analyze the code at the source code level, compiled code level, or bytecode level.
Static analysis is typically a combination of control flow and data flow analyses. This technique helps auditors identify vulnerabilities by analyzing how the code works rather than what it produces when executed. Static analysis is particularly useful for identifying vulnerabilities that cannot be easily detected through testing.
By applying static analysis, auditors can identify security weaknesses such as SQL injection, cross-site scripting, and buffer overflow vulnerabilities.
Automated fuzzing
In a cybersecurity audit, fuzzing is an automated software testing technique that provides invalid, unexpected, or random data as input to a computer program. The program is then monitored for exceptions such as crashes, failing built-in code assertions, or potential memory leaks.
Fuzzing is especially relevant to software projects that are exposed to arbitrary input from untrusted sources, such as smart contracts on the blockchain. Smart contracts can be interacted with on the blockchain with random inputs without a valid reason or expectation.
Fuzzing can effectively discover edge cases, potential buffer overflows, and other types of unexpected or malicious behavior. Performing it, auditors can help ensure the project code is secure and ready for deployment.
Automated symbolic verification
Symbolic checking is a powerful technique for verifying program correctness without requiring exhaustive testing or execution. It involves representing sets of states and transitions using symbolic inputs instead of enumerating individual states/transitions separately. This method is also known as model checking or property checking.
Symbolic checking relies on precise mathematical languages to formulate a problem in logic and verify whether a structure satisfies a given logical formula. By representing the graph implicitly using a formula in quantified propositional logic, this method avoids explicitly constructing the graph for finite state machines (FSMs). Also, by representing the graph implicitly using logical formulas or binary decision diagrams (BDDs), auditors can traverse the state space more efficiently, helping to address the state explosion problem.
This makes it a valuable technique for identifying security weaknesses, especially in complex software projects. Symbolic checking helps auditors to traverse the state space more efficiently, providing a comprehensive evaluation of a software project's security posture and helping to address the state explosion problem.
Automated formal verification
Formal verification is a technique of verifying program correctness by proving or disproving the algorithms underlying a system for a certain formal specification or property using formal mathematics methods. Formal verification is highly effective at detecting complex fundamental bugs that are difficult to detect manually or using simpler automated tools.
Verification can be done through theorem proving, model checking, an abstract interpretation, or other formal methods. So the process of formal verification involves creating a mathematical model of the software, along with a set of logical rules for proving that the model is correct. This model is then tested to ensure that it conforms to the formal specification of the software.
This makes formal verification a valuable technique in conducting a comprehensive cybersecurity audit, ensuring the security and correctness of fundamental algorithms of software systems.
Manual analysis
Manual analysis is a critical component of a comprehensive cybersecurity audit and complementary to automated analysis using tools. While automated analysis is cheap, fast, and deterministic, it is limited to the tools' constraints.
On the other hand, manual analysis is expensive, slow, and non-deterministic, but it is necessary for evaluating business logic and application-level constraints, which is where many serious vulnerabilities are found. Manual analysis requires human expertise in cybersecurity and can help auditors better understand a system's security posture.
Benefits of a cybersecurity audit

- Protecting against financial and reputational threats. Identify security vulnerabilities in software projects that could lead to financial losses or damage a company's reputation. Businesses can prevent costly breaches and protect their brand by addressing these vulnerabilities.
- Improving the quality of solutions. Identify and address software design flaws, coding errors, and other issues that could compromise the security and reliability of a software solution. By improving the quality of their solutions, businesses can enhance customer satisfaction and build trust.
- Increasing the value of solutions. Provide assurance to customers that a software solution is secure and has been independently verified. This can increase the solution's value and help differentiate it from competitors.
- Enhancing customer loyalty. Enhance customer loyalty and attract new customers by demonstrating a commitment to cybersecurity and taking proactive measures to protect customer data.
- Mitigating legal liabilities. Identify potential security risks that may lead to legal liabilities, such as breaches of data protection regulations. A company can avoid costly legal proceedings and penalties.
- Improving regulatory compliance. Ensure that a company complies with industry-specific regulations and standards and general data protection laws. This can reduce fines and reputational damage from non-compliance.
- Future-proofing solutions. Identify potential security weaknesses that attackers may exploit in the future. By addressing these weaknesses proactively, a company can future-proof its solutions and stay ahead of evolving threats.
Internal vs. external security audits
An internal security audit is essential and necessary and can never be superfluous. Moreover, constant internal audits help not only to increase code quality at minimal cost but also to expand the expertise of the company and its employees.
However, cybersecurity audits by third-party experts will not only be of higher quality but also bring plenty of additional benefits, starting from obtaining the appropriate certificates upon passing this audit, which can be very good for the reputation and value of the company. For example, this can be especially important in the blockchain industry, the credibility of which has not yet been established the same as more traditional types of software. So getting audited in this area by expert third-party companies can play a key role in the success of your product.
Internal audits pros and cons
| Internal Audits Pros | Internal Audits Cons |
|---|---|
| Cost-Effective. Performing internal audits can be more cost-effective than hiring external auditors. | Limited Perspective. Internal auditors may have a biased perspective and may overlook certain security risks due to their familiarity with the company's systems. |
| In-depth Knowledge. Internal auditors deeply understand the company's operations, infrastructure, and culture, which can help them identify probable security risks. | Limited Expertise. Internal auditors may not have the same level of expertise and experience as external auditors who specialize in security. |
| Immediate Response. Internal auditors can respond to security incidents quickly and efficiently since they are familiar with the company's systems. | Limited Resources. Internal auditors may have limited resources, such as access to specialized tools and techniques, which can limit the scope and effectiveness of the audit. |
| Easy Communication. Internal auditors can communicate easily with the company's other staff and management, which can help facilitate the audit process. | Conflict of Interest. Internal auditors may have a conflict of interest if they are responsible for implementing and auditing security controls. |
| Better Control. Internal audits can give the company better control over the audit process and provide more flexibility regarding audit scope and timelines. | Lack of Objectivity. Internal auditors may lack objectivity and independence in their reporting due to their close relationship with the company. |
External audit pros and cons
| External Audit Pros | External Audit Cons |
|---|---|
| Expertise and Experience. External auditors have specialized expertise and experience in conducting security audits, which can help them identify potential security risks more effectively. | Costly. External audits can be more expensive than internal audits, especially if the audit scope is broad and complex. |
| Independence. External auditors can provide an independent and objective evaluation of the company's security posture. | Time-Consuming. External audits may take longer to complete since external auditors are unfamiliar with the company's systems and operations. |
| Specialized Resources. External auditors may have access to specialized tools and techniques that can enhance the scope and effectiveness of the audit. | Inconvenient. External audits can disrupt the company's operations and may require staff to provide access to systems and data. |
| Unbiased Perspective. External auditors can bring an unbiased perspective to the audit since they are not familiar with the company's systems and operations. | Limited Knowledge. External auditors may not have a deep understanding of the company's culture and infrastructure, which can limit their effectiveness. |
| Reputation. Obtaining certifications from accredited external auditors can enhance the company's reputation and value. | Lack of Control. External audits can give the company less control over the audit process and scope. |
Cybersecurity audit vs. assessment
A cybersecurity audit evaluates an organization's information security infrastructure to identify potential vulnerabilities and assess whether existing security measures are effective. It is a point-in-time evaluation that provides a snapshot of the system's current state, identifies gaps, and makes recommendations for improvement.
A cybersecurity assessment, on the other hand, is a continuous process that includes the audit or at least works with its results. It involves ongoing monitoring and analysis of an organization's information security infrastructure to ensure and maintain the desired level of security by implementing appropriate processes, practices, and tools.
Together, these processes help organizations holistically defend against cybersecurity threats and mitigate the risks associated with those threats.
How to perform a cybersecurity audit?
If you are interested in cybersecurity audit consulting to get the highest quality and depth of the audit, you still need to prepare for it. Here, we'll cover the main points, which will greatly simplify the work of third-party experts, saving you a lot of time and money and improving the result.
Preparing for an audit
- Fix and clean up. Include and fix every last compiler warning, increase the coverage of unit and functional testing, and remove dead code, obsolete branches, unused libraries, and other extraneous weight.
- Documentation. Describe what the product does, who uses it, and why and how it works. Add comments about the intended behavior according to the code. Name and describe your tests and results, both positive and negative. Include past reviews and errors.
- Resource provision. Document the steps to create a build environment from scratch on a computer that is completely disconnected from your internal network. Include external dependencies. Document the build process, including debugging and test environment. Document the process and deployment environment, including any specific versions of external tools and libraries for the process.
If you decide to do your internal audit to save money and time and expand your expertise, you'll need these preparations, too. However, you will also be helped by the cybersecurity audit checklist following you will not miss any of the critical points.
Conducting an audit
- Audit scope. Define the audit objectives and areas, and identify what is included in the audit, such as applications, systems, processes, or networks.
- Audit goals. Determine the desired outcomes of the audit, such as identifying vulnerabilities, assessing the effectiveness of existing security controls, or assessing compliance with industry standards or regulations.
- Audit timeline. Establish the timeline for the audit, including the start and end dates and any key milestones or deadlines.
- Audit costs. Determine the budget for the audit, including any necessary resources.
- Choosing audit type. Determine the type of audit that best meets the current state of your project and follows its needs.
- Choosing audit techniques. Identify the appropriate audit techniques to be used, such as automated testing, manual testing, automated static analysis, еtс.
- Audit reports. Develop the audit reports, including a summary of the objectives, findings, recommendations, etc.
- Audit findings classification. Classify the vulnerabilities found during the audit into different categories, which helps to understand the nature of the vulnerability, potential impact/severity, impacted project components/functionality, and exploit scenarios. Common categories include access controls, auditing and logging, authentication, configuration, cryptography, data exposure, data validation, denial of service, error reporting, patching, session management, timing, and undefined behavior.
- Audit findings likelihood/difficulty. Determine the likelihood or difficulty of each finding. Common levels include Low, Medium, and High, depending on the ease of exploitation, complexity, and potential impact.
- Follow-up actions. Develop a plan for addressing the audit findings, including prioritization of remediation efforts, allocating resources, and establishing a schedule for follow-up actions.
Best cybersecurity audit tools
Tools for scanning web vulnerabilities
Web applications are a popular target for attackers, making it essential to scan for web vulnerabilities regularly. Tools for scanning web vulnerabilities include both commercial and open-source software. These tools aim to identify vulnerabilities and help in fixing them.
Best practices for scanning web vulnerabilities include following the guidelines set forth by the Open Web Application Security Project (OWASP). This includes using the latest version of the OWASP Top Ten, a list of the most critical web application security risks, as a baseline for scanning web vulnerabilities. Additionally, it is important to perform scans regularly, especially after significant changes to web applications, and to use a combination of automated and manual scans to maximize coverage.
Some key tools for scanning web vulnerabilities include Nikto, Nexpose, Paros Proxy, and Acunetix. Nikto is an open-source web server scanner that can identify over 6,700 potentially dangerous files and programs on web servers. Nexpose is a vulnerability scanner that can identify vulnerabilities across various assets, including web applications. Paros Proxy is a web application security scanner that works as a proxy server between the user and the scanned application. Acunetix is a web vulnerability scanner that can detect over 4,500 vulnerabilities, including SQL injection and cross-site scripting (XSS).
Password auditing and packet sniffers cybersecurity tools
Password auditing and packet sniffers cybersecurity tools are used to test the strength of passwords and monitor network traffic for malicious activity.
Best practices in this area include regular password policy updates, training employees on password best practices, and monitoring network traffic for unauthorized activity. One common standard used in this area is the National Institute of Standards and Technology (NIST) Special Publication 800-63B, which provides digital identity and authentication guidelines. Additionally, the Payment Card Industry Data Security Standard (PCI DSS) requires regular password changes, strong passwords, and the encryption of transmitted data.
Some key tools in this area include Cain and Abel, and John the Ripper. Cain and Abel is a powerful password recovery tool that can crack many different types of passwords. John the Ripper is a password cracker that uses brute force techniques to crack passwords.
Penetration testing
Penetration testing is a proactive approach to cybersecurity that allows organizations to discover vulnerabilities before cybercriminals can exploit them. The goal of penetration testing is to assess the security of a system and to provide recommendations to improve the organization's security posture.
Best practices for penetration testing include performing regular testing, testing from different perspectives, testing from different locations, and using different devices. Also, good to delegate testing to a third-party organization to provide an unbiased evaluation of the security infrastructure.
Standards such as the Penetration Testing Execution Standard (PTES) guide the methodology and procedures to be followed in penetration testing. Compliance with PTES helps ensure that penetration testing is conducted thoroughly and consistently, providing reliable results and actionable recommendations.
Some commonly used penetration testing tools include Kali Linux, Metasploit, and Nessus Professional. Kali Linux is an open-source penetration testing platform with a wide range of tools for testing different systems and networks. Metasploit is a powerful framework for exploiting vulnerabilities and testing the security of systems. Nessus Professional is a comprehensive vulnerability scanning and assessment tool that provides in-depth analysis of vulnerabilities and remediation advice.
Cybersecurity tools for network defense
Cybersecurity tools for network defense help protect an organization's systems and data from cyber threats. These tools include firewalls, intrusion detection and prevention systems, virtual private networks (VPNs), and security information and event management (SIEM) software.
Implementing a defense-in-depth strategy, which involves layering multiple security measures to protect against threats, is a best practice for using cybersecurity tools for network defense. Other best practices include using up-to-date software and firmware, keeping logs of all network activity, monitoring network traffic for suspicious behavior, and regularly reviewing and updating security policies.
Organizations can follow industry standards and frameworks such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework to ensure the effective use of cybersecurity tools for network defense, which provides guidelines and best practices for managing and reducing cybersecurity risk. Another useful framework is the Center for Internet Security (CIS), which outlines specific actions that organizations can take to improve their cybersecurity posture.
Some key cybersecurity tools for network defense include Forcepoint offers a range of network security solutions for cloud and on-premises environments. Snort is a free and open-source network intrusion detection and prevention system. Wireshark is a network protocol analyzer that can monitor network traffic and detect malicious activity. Tcpdump is a command-line tool that captures network traffic and analyzes it for any security vulnerabilities.
Some other popular tools include Netstumbler, Aircrack-ng, and KisMAC. Netstumbler is a popular Windows tool for wireless network mapping and detection of access points and stations, Aircrack-ng is a wireless network security testing tool that can crack WEP and WPA keys and perform other attacks on wireless networks, and KisMAC is a wireless network discovery and assessment tool for macOS.
Encryption cybersecurity tools
Encryption cybersecurity tools can help prevent unauthorized access to data and provide an additional layer of protection against various types of cyber threats.
Best practices for using encryption cybersecurity tools include implementing a strong encryption algorithm, regularly changing encryption keys, ensuring the physical security of the storage media, and enforcing a policy of "need-to-know" access to sensitive data. In addition, several industry standards and frameworks provide guidance on how to implement encryption technologies effectively. These include the NIST Cybersecurity Framework, the International Organization for Standardization (ISO) 27001, and the PCI DSS.
Also, there are encryption cybersecurity tools TrueCrypt, KeyPass, Tor. TrueCrypt is an open-source disk encryption software that can create virtual encrypted disks, encrypt entire partitions or storage devices, and encrypt individual files. KeyPass is a password manager that encrypts and stores passwords, credit card information, and other sensitive data. Tor is a browser that uses union protocol, protecting users' privacy and security.
Tools for monitoring network security
Tools for monitoring network security help organizations detect and respond to cyber threats in real-time. These tools include log analyzers, network traffic analyzers, etc.
Best practices for using cybersecurity tools for monitoring network security include regular monitoring of network traffic, maintaining logs of all network activity, implementing real-time alerting mechanisms, reviewing and updating security policies, and establishing incident response protocols. Here you will find useful the same frameworks and standards as before NIST Cybersecurity Framework, the ISO 27001, the CIS, etc.
Some key cybersecurity tools for monitoring network security include Splunk, POf, Argus, and Nagios. Splunk provides advanced analytics and visualization capabilities for log data. POf is a powerful and flexible network traffic analyzer. Argus provides network flow analysis and packet capture capabilities. And Nagios offers network monitoring and alerting capabilities.
Cybersecurity tools for detecting network intrusions
Cybersecurity tools for detecting network intrusions are designed to identify potential threats and suspicious behavior in network traffic. By monitoring network activity and detecting anomalies, these tools help to prevent attacks and ensure the security of an organization's data and systems.
Best practices for using cybersecurity tools for detecting network intrusions include using a layered approach to security, ensuring all software and firmware are up-to-date, monitoring network activity in real-time, reviewing and updating security policies regularly, and limiting access to sensitive data to authorized individuals. Here are NIST Cybersecurity Framework, the ISO 27001, the PCI DSS, and the CIS again.
Here have Snort and Forcepoint again. Also, we have OSSEC and GFI LanGuard. Snort can detect a wide range of attacks and malicious activities in network traffic, including network scans, protocol violations, and buffer overflow attempts. Forcepoint also can offer a range of network security solutions for cloud and on-premises environments, using behavioral analytics to identify and block threats, and also provides real-time visibility into network activity. OSSEC provides host-based intrusion detection and log analysis. GFI LanGuard is a network security scanner that can identify vulnerabilities in operating systems, applications, and network devices.
Best cybersecurity practices
Of course, there can be a huge number of specific standards, techniques, and tools. So it would be great to know the practices that enable them and use them for the most critical aspects of security. Here are the key practices every company should implement to take cyber security to a whole new level.
Use an encrypted email or messaging server
Encrypting email or messaging servers is a critical cybersecurity practice that ensures that all data transmitted or received is protected from interception and unauthorized access. Encryption technology is used to encode messages to prevent eavesdropping and tampering. The technology enables only authorized users to read the content, which can help protect sensitive information. Implementing encrypted email or messaging servers can also help maintain compliance with relevant data protection regulations, such as GDPR or CCPA. For example, ProtonMail is a secure email service that uses end-to-end encryption to protect users' communications.
Adopt an independent and decentralized cybersecurity strategy
A standalone cybersecurity strategy enables an organization to develop comprehensive security policies and procedures, allocate adequate resources, and create a dedicated security team to manage security-related issues. Making it decentralized helps to spreads the responsibility for cybersecurity across an organization rather than relying on a single point of control. This approach can make it more difficult for attackers to exploit a single vulnerability to gain access to an entire network. A decentralized strategy also allows organizations to respond more effectively to cyber incidents, as employees are empowered to take action in the event of an attack.
Develop an effective cyber incident response plan
Developing a cyber incident response plan is critical to minimize damage and ensure speedy recovery in the event of a cyber attack. The plan should outline the steps to be taken in the event of a breach, including identifying the type of attack, containing the breach, and recovering from the attack. The plan should also include a clear chain of command, procedures for communication, and a strategy for post-incident analysis. For example, the SANS Institute provides great guidelines for creating a comprehensive incident response plan.
Train employees on cybersecurity awareness
Employees are often the weakest link in an organization's cybersecurity defenses. Educating employees on cybersecurity best practices can help reduce the risk of a successful cyber attack. Cybersecurity training can include password management, recognizing phishing emails, and safe browsing practices. For example, the Cybersecurity and Infrastructure Security Agency (CISA) provides free cybersecurity training resources for organizations of all sizes.
Implement a zero trust architecture
Zero trust architecture is an approach to cybersecurity that assumes all users, devices, and applications are potential threats and should be verified before being granted access to resources. This approach involves authenticating and authorizing access for each user and device, as well as monitoring activity to detect potential threats. Google's BeyondCorp framework is a good example of a zero-trust architecture focusing on device and user identity to secure resource access.
Ensure a strong password protocol
Strong password protocols are essential for preventing unauthorized access to networks and devices. This involves creating complex passwords that combine upper and lower-case letters, numbers, and special characters. Passwords should be changed regularly and not be reused across multiple accounts. Two-factor authentication can also be implemented to provide an additional layer of security. For example, the National Cyber Security Centre (NCSC) the whole separate guides for creating strong passwords.
Enable automatic operating system updates
Automatic operating system updates are an essential cybersecurity practice for all companies. Regularly updating operating systems helps to ensure that any security vulnerabilities are addressed promptly and that the system remains protected from the latest threats. Enabling automatic updates ensures that these updates are installed as soon as they become available without requiring any additional effort from the user. This can help protect against attacks that exploit known vulnerabilities in older software versions.
Some examples of implementing automatic operating system updates include Microsoft Windows Update and Apple Software Update, which provide automatic updates for Windows and macOS. Additionally, Linux-based operating systems such as Ubuntu also have automatic update features that can be configured to run at regular intervals. It is important to ensure that all devices connected to the company network, including laptops, desktops, and mobile devices, have automatic updates enabled to ensure that they are protected from the latest threats.
Use a secure connection for company devices
To protect against cyber attacks and data breaches, ensuring that all company devices are connected to a secure network is crucial. This includes using secure protocols such as HTTPS, SSL, or VPNs when accessing company resources. Some examples of secure connection tools and technologies include Cisco AnyConnect VPN, Fortinet Secure Access, and OpenVPN.
Back data up to an encrypted drive
Backing up data ensures that an organization's data is protected during a cyber-attack or other disaster. But storing backup data on an encrypted drive provides an extra layer of security, preventing unauthorized access and ensuring confidentiality. Some examples of encrypted drive technologies include VeraCrypt, BitLocker, and DiskCryptor.
Keep antivirus software up-to-date
Antivirus software is a fundamental tool for protecting against malware, viruses, and other cyber threats. However, antivirus software must be updated with the latest virus definitions and security patches to be effective. Failure to update antivirus software can leave systems vulnerable to new and emerging threats. Examples of popular antivirus software include Norton Antivirus, McAfee, and Kaspersky.
Limit the number of network administrators
Limiting the number of network administrators reduces the risk of insider threats and accidental security breaches. It ensures that only authorized individuals can access sensitive network resources and monitor and audit network activity to identify suspicious behavior. Examples of tools and technologies for limiting network administrators include role-based access controls and privileged access management solutions such as BeyondTrust and CyberArk.
Enable auto-lock for company devices
Enable auto-lock features on all devices to ensure that devices are automatically locked when not in use, requiring a password or other form of authentication to unlock them. Examples of auto-lock tools and technologies include Microsoft Intune, MobileIron, and AirWatch.
Dispose of equipment and data securely
Decommissioning or disposing of company devices or data must ensure that all data is securely erased or destroyed to prevent it from falling into the wrong hands. This can be accomplished using data destruction tools such as Blancco, Secure Erase, or DBAN.
Conduct regular cybersecurity assessments
New types of vulnerabilities, and the sophistication of cyber-attacks are on the rise, so an audit, once performed, can quickly become irrelevant. Regular security audits help organizations ensure that their security knowledge is actual and complete at any given time. This should include a comprehensive review of all cybersecurity practices and technologies and a test for vulnerabilities and weaknesses. Examples of suitable tools and technologies include Nessus, OpenVAS, and Qualys.
Employ third-party penetration testing services
Penetration testing is essential for identifying potential vulnerabilities and weaknesses in an organization's cybersecurity defenses. Employing cybersecurity audit services that provide expert penetration testing can help ensure that assessments are objective and comprehensive and can provide an independent perspective on an organization's cybersecurity posture. Examples of third-party penetration testing services include Coalfire, Rapid7, and Trustwave.
Bug bounty
A bug bounty program is a cybersecurity initiative that rewards individuals for identifying and reporting security vulnerabilities in an organization's systems and software. Bug bounty programs can help continuously identify and mitigate potential vulnerabilities before cybercriminals exploit them without hiring the whole cyber security. Examples of organizations that have implemented bug bounty programs include Apple, Google, Microsoft, and many others companies.
Summary
Cybersecurity is crucial in today's digital landscape, and a cybersecurity audit is essential in protecting an organization's systems and data. However, conducting an audit in-house may not produce the desired results.
External cybersecurity audits can offer a more cost-effective and result-efficient solution. Third-party professionals can bring their expertise and provide a fresh perspective on potential vulnerabilities and threats which internal teams may overlook. This can enhance an organization's overall security posture and help identify areas for improvement.
Don't leave your cybersecurity to chance. In addition to the comprehensive information you already get, you can always contact us for your free consultation and get profound benefits for your organization.