In the ever-evolving landscape of technology and data, the significance of safeguarding sensitive information becomes more evident. As data volumes grow, big data is becoming a pivotal asset for organizations across diverse industries. However, with the vast potential of big data come various security challenges that require diligent attention and strategic solutions.
In this article, we delve into big data security and explore the best practices and analytics methods for organizations to fortify their data and detect potential threats and malicious activities. Discover how big data security works and what are some of the challenges down this road.
What is big data and big data security
Big data combines structured, semi-structured, and unstructured data collected by organizations. It can be mined for information and used in machine learning (ML) projects, predictive modeling, and other advanced analytics applications.
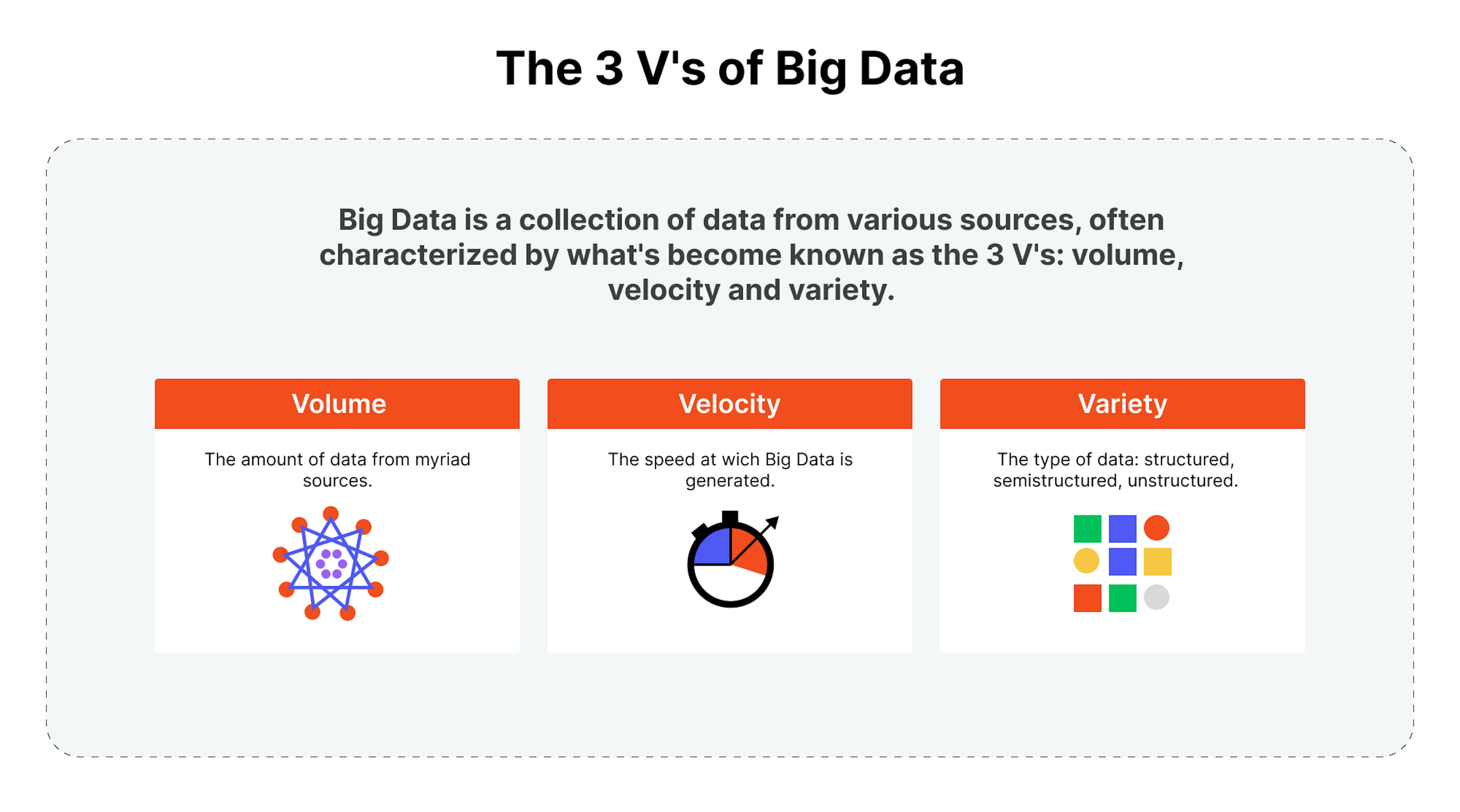
The processing and storing of big data has become a common component of data management architectures in organizations, combined with tools that support big data analytics. There are 3 Vs are often used to describe big data:
- the large volume of data in many environments;
- the wide variety of data types frequently stored in big data systems:
- the velocity at which much data is generated, collected, and processed.
Big data security refers to the measures and practices implemented to protect large volumes of data against unauthorized access, breaches, and malicious activities. Securing big data involves 3 main phases:
- Ensuring the safe transfer of data from source locations, typically in the cloud, for storage or real-time ingestion.
- Safeguarding data within the storage layers of the big data pipeline.
- Maintaining the privacy of output data, including reports and dashboards, which contain insights obtained from data analysis using tools like Apache Spark. Establishing a secure foundation through building a data warehouse is essential, as it provides a centralized repository that supports these security measures effectively.
Why is it important to secure big data
Almost every organization today considers adopting big data because they see its potential and are trying to exploit it. Regardless of the organization's size, everyone is trying to protect their data.
According to IBM and the Ponemon Institute's 2023 report, the average cost of a data breach in 2023 will reach US$ 4.45 million, seeing an increase of 2% over 2022 (US$ 4.35 million).
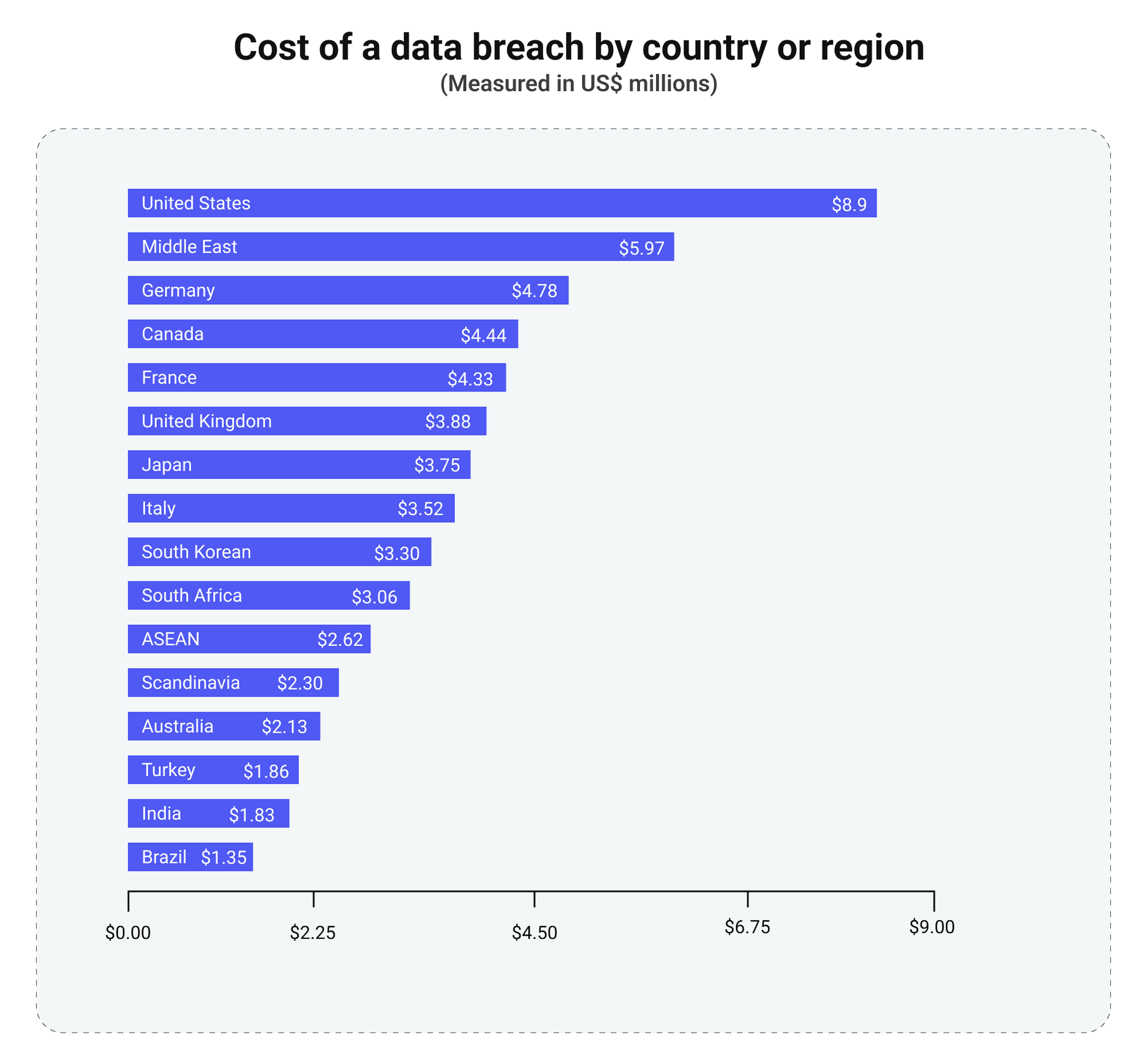
Data breaches have become more frequent, resulting in increased legal actions and penalties, particularly due to stricter data privacy regulations in regions like the EU, California, and Australia (e.g., GDPR, CCPA, and CSP234). Additionally, companies in regulated sectors, such as healthcare and credit card processing, face industry-specific standards like HIPAA and PCI/DSS.
Emerging threats like social engineering, ransomware, and advanced persistent threats (APTs) pose significant challenges as they are hard to defend against and can cause severe data damage.
Solving data security issues is complex; merely adding more security tools isn't enough. Security and tech departments must collaborate creatively to address these challenges effectively. Here, it is crucial to evaluate the cost-effectiveness of current security measures and assess the potential returns on further investments.
What are the benefits of big data for business
Understanding the benefits of big data security is essential if an organization is looking to leverage its potential. Here are some key benefits:
- Better decision-making. Businesses can benefit from big data analytics by gaining valuable insights and patterns that can assist them in making informed and data-driven decisions. Analysis of large volumes of data enables businesses to identify trends, customer preferences, market opportunities, and potential risks, resulting in more effective decision-making.
- Improved operational efficiency. Big data analytics can optimize business operations by identifying inefficiencies, bottlenecks, and areas for improvement. Businesses can streamline processes, reduce costs, and enhance productivity by analyzing data from various sources.
- Enhanced customer understanding. Big data allows businesses to gain a deeper understanding of their customers. Companies can identify patterns, preferences, and behaviors to personalize marketing campaigns, improve customer experiences, and build stronger customer relationships.
- Targeted marketing and advertising. Big data analytics helps businesses target marketing efforts better by analyzing customer data and market trends. It leads to personalized campaigns, higher conversion rates, and improved ROI.
- Competitive advantage. Leveraging big data analytics gives businesses a competitive edge. It helps them spot market trends, track competitors, and make strategic decisions to outperform rivals. Additionally, big data uncovers new market prospects and fuels product and service innovation.
- Risk management. Big data analytics helps businesses with risk identification and mitigation. Through data analysis from diverse sources, companies can uncover potential fraud, security threats, and operational risks, and mitigate these challenges proactively.
- Product and service innovation. Big data has the potential to fuel innovation by offering businesses valuable insights into customer requirements, market dynamics, and emerging technologies. Through data analysis, companies can pinpoint market opportunities, create novel products and services, and enhance existing ones to cater to customer needs.
Overall, big data offers businesses the potential to gain valuable insights, improve decision-making, enhance operational efficiency, and gain a competitive advantage in the market.
What is the architecture of big data security
Let's start with the difference between big data security and big data security management. This is necessary because some users require clarification on these two concepts.
In this article, we mostlyfocus on big data security. The architecture of big data security and big data security management are related concepts, but they are not the same thing; the difference between them:
| Big data security | Big data security management |
|---|---|
| Big data security refers to the security measures and mechanisms implemented within a big data environment to protect the data, infrastructure, and applications involved in big data processing. | Big data security management is a broader concept that encompasses not only the technical security measures within a big data environment but also the policies, procedures, and governance practices that an organization puts in place to manage and oversee big data security. |
| It focuses on the technical aspects of securing the various components of a big data ecosystem, including data storage systems (e.g., Hadoop clusters, data warehouses), data processing engines, data pipelines, and the data itself. | It involves strategic planning, risk assessment, compliance management, and overall coordination of security efforts related to big data. |
| Big data security includes data encryption, access controls, authentication, authorization, monitoring, threat detection, and data masking specific to the big data environment. | Big data security management implies aligning security practices with an organization’s overall security strategy and ensuring that security controls are effectively implemented and maintained over time. |
Big data security focuses on the technical aspects of securing big data systems. In contrast, big data security management includes a more holistic approach that involves strategic planning, policy development, risk management, compliance, and oversight of security practices within the context of big data. Both are essential to the security and integrity of big data environments in organizations.
The architecture of big data security refers to the structure and components put in place to ensure security and protection. It involves various stages and measures to minimize risks and safeguard sensitive data. While the specific architecture may vary depending on the organization and its requirements, here are some standard components and considerations:
- Data encryption is vital in big data security. It converts data into code that requires access decryption and boosts data protection during storage, transmission, and processing, deterring unauthorized access or tampering.
- Access control manages data access and actions via authentication, user roles, and permissions, ensuring only authorized individuals can interact with specific data.
- Data masking and anonymization protect sensitive data by substituting it with fictitious or scrambled information. This prevents unauthorized access and misuse of sensitive data and helps maintain confidentiality.
- Data loss prevention (DLP) measures prevent data loss or leaks, whether accidental or intentional, through monitoring, policy enforcement, and technology like data loss prevention software and network monitoring.
- Secure data storage safeguards data at rest through secure systems, encryption, backups, and disaster recovery plans.
- Network security is vital for protecting data during transmission. It involves secure communication protocols, firewalls, intrusion prevention, and network configurations to thwart unauthorized access and data interception.
- Auditing and monitoring track data-related activities, spotting suspicious actions, upholding security policies, and detecting potential breaches.
- Security analytics employs advanced methods to spot and address security threats and irregularities. This encompasses scrutinizing data patterns, recognizing potential risks, and proactively addressing them.
It is important to note that the architecture of big data security is a complex and evolving field, and organizations need to continuously assess and update their security measures to stay ahead of emerging threats and vulnerabilities.
How big data security works
Big data security aims to prevent unauthorized access and intrusions using firewalls, robust user authentication, end-user training, and intrusion detection and prevention systems (IDS/IPS). Data encryption is also vital for safeguarding data in transit and at rest.
However, big data environments introduce a higher level of complexity because security tools must operate across three distinct data stages that are not typically encountered in traditional network security:
Stage 1: Data sources
Big data derives from diverse sources and formats, encompassing user-generated data like CRM or ERM data, transactional databases, and vast volumes of unstructured data. For example, emails and social media posts — machine-generated data, including logs and sensor data, further compound the complexity. Ensuring data security in transit, from source to platform, is paramount.
Stage 2: Stored data
Protecting stored data necessitates mature security toolsets, including encryption at rest, robust user authentication, and intrusion prevention. Companies must deploy these security measures across distributed clusters with numerous servers and nodes. Moreover, security tools must extend their protection to log files and analytics tools operating within the platform.
Stage 3: Output data
Big data platforms are designed to perform sophisticated analytics on extensive datasets, and generate valuable insights delivered through applications, reports, and dashboards. However, this intelligence becomes an attractive target for intrusions. That is why encrypting output data, alongside data ingress, and ensuring compliance at this stage is critical.
What types of data security controls
To secure data and prevent data breaches, we recommend following these control measures.
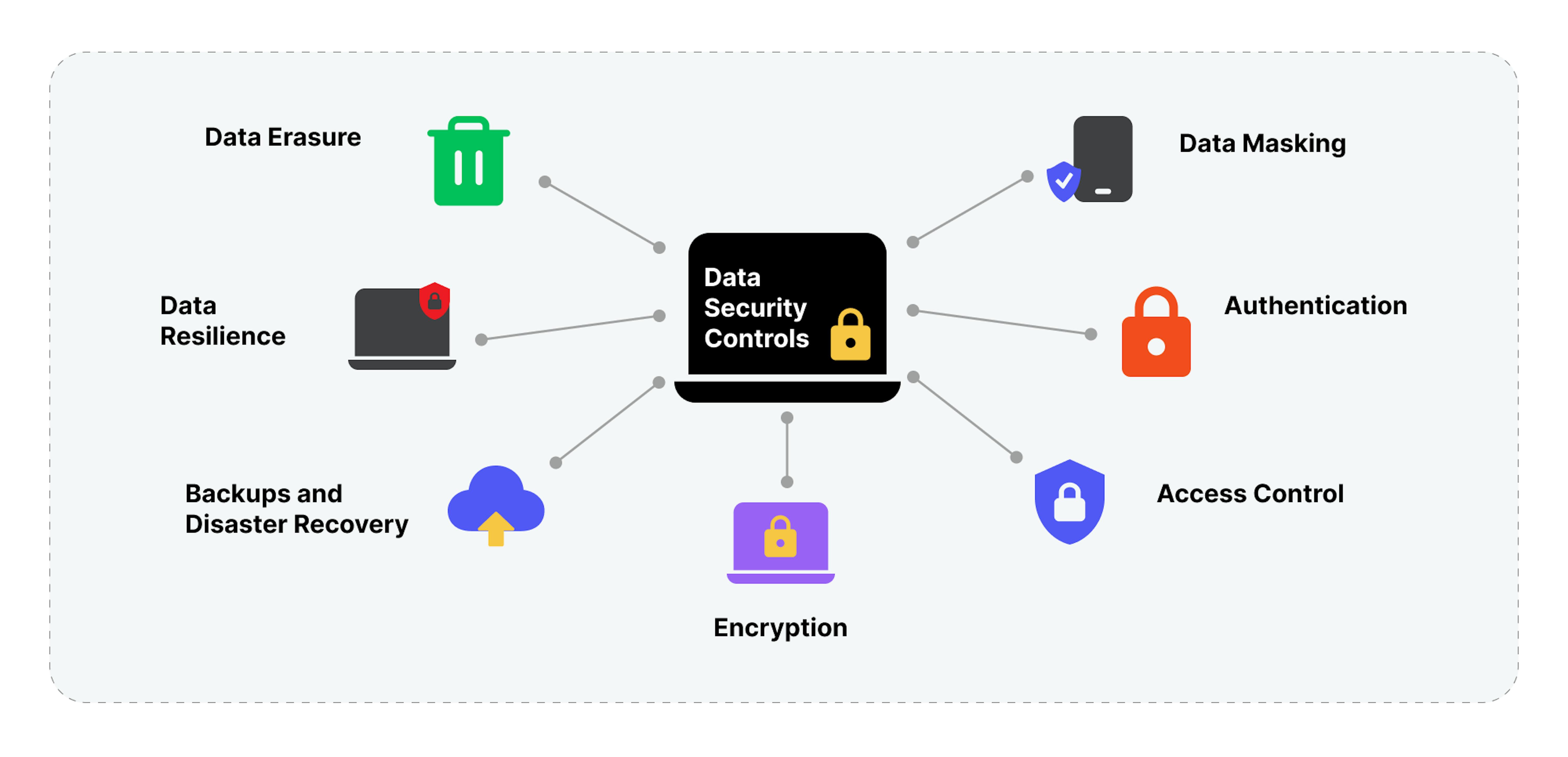
Access control
In order to secure data, it is important to limit both physical and digital access to central systems and data. The goal is to ensure that all computers and gadgets are password-protected and that physical locations are only accessible to authorized individuals.
Authentication
Before granting access to data, implement authentication measures, such as access restrictions and proper identification of people. Biometrics, passwords, PINs, security tokens, and swipe cards are examples of passwords and PINs.
Backups and disaster recovery
Effective security entails having a plan to access data safely during system failures, disasters, data corruption, or breaches. To facilitate recovery, a backup data copy must be stored in a separate format, such as a hard drive, local network, or the cloud.
Data erasure
Regularly and properly disposing of data is essential. Data erasure, which employs software to completely wipe data from any storage device, is a more secure method than conventional data wiping. It guarantees that data cannot be retrieved, preventing it from ending up in unauthorized hands.
Data masking
Data masking software uses proxy characters to hide letters and numbers, effectively concealing the information. In the case of unauthorized access, the data remains concealed, becoming visible solely when an authorized user accesses it.
Data resilience
Robust security measures in place allow you to endure or bounce back from failures, prevent disruptions caused by power outages, and minimize the impact of natural disasters that could compromise data security. You can effectively enforce data privacy by integrating resilience into your hardware and software.
Encryption
Through encryption keys, a computer algorithm transforms text characters into an unintelligible form, ensuring that only authorized individuals with the necessary keys can unlock and access the content. To a certain degree, it is essential to secure various forms of data, including files, databases, and email communications.
What are the major big data security challenges
The continuously growing volume of data offers advantages and drawbacks. Enhanced data analysis can lead to better decision-making for businesses, but it also introduces security concerns, especially when handling sensitive information.
Here are some of the challenges in big data security that organizations need to address.
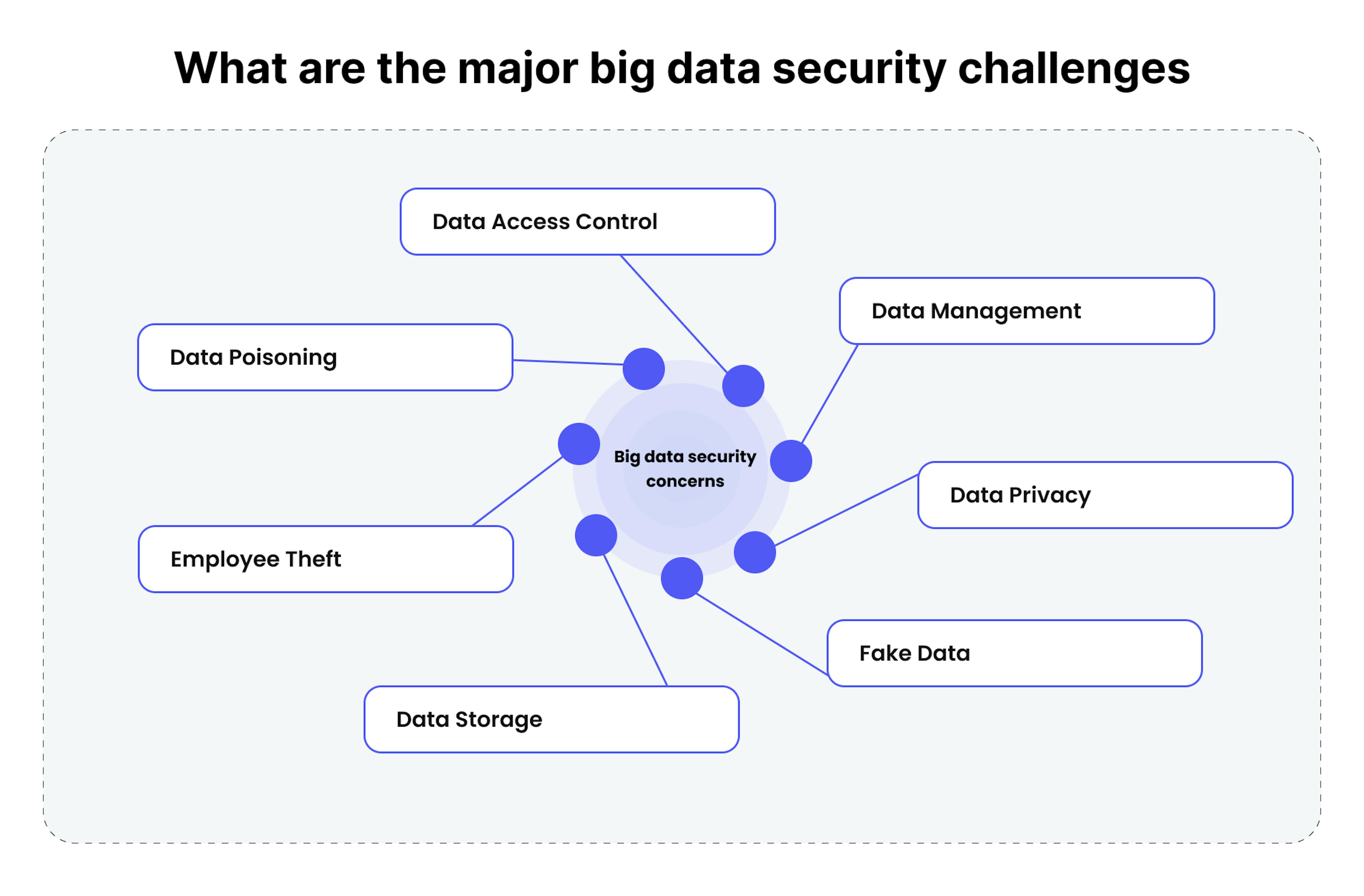
Data storage
Businesses increasingly adopt cloud data storage for streamlined operations, but this convenience comes with security risks. Even minor lapses in data access control can expose sensitive information. As a result, many large tech companies opt for a combination of on-premise and cloud data storage to balance security and flexibility. While critical data is stored in on-premise databases, less sensitive information is placed in the cloud for accessibility. However, securing on-premise databases requires cybersecurity expertise, which increases management costs. Companies must carefully assess security risks and not rely solely on cloud storage.
Fake data
Fake data generation poses a significant threat, as it consumes valuable time that could be used to address more pressing issues. The potential impact of inaccurate information at scale can be detrimental, leading to unnecessary actions that disrupt production and critical processes. Companies should thoroughly examine their data to address this challenge and routinely assess data sources, using various test datasets to evaluate ML models and detect anomalies.
Data privacy
This major concern in the digital age calls for strict measures to protect sensitive personal information from cyber threats, breaches, and data loss. Enterprises should uphold strong data confidentiality principles, and utilize compliant cloud access management services to bolster data safeguarding. These standards should be addressed by crucial practices such as extensive data awareness, effective data repository administration and backups, network security against unauthorized entry, regular risk evaluations, and consistent user training on data confidentiality and security.
Data management
A security breach can have severe repercussions, including the exposure of critical business information within a compromised database. To ensure data security, deploying highly secure databases with various access controls is essential. Robust data management systems offer extensive security measures, including data encryption, segmentation, partitioning, secure data transfer, and trusted server implementation.
Data access control
Effectively controlling data access, especially in large organizations with numerous employees, is challenging but crucial for preserving data integrity and privacy. Shifting to cloud-based Identity Access Management (IAM) solutions has simplified access control processes. IAM manages data flow through identification, authentication, and authorization, following ISO (27001, 27002, 22301, 27701, 15408) standards to ensure best practices are met.
Data poisoning
ML solutions, like chatbots, continuously improve through interaction with vast datasets, but this progress can be exploited through data poisoning attacks. This tampering with training data can compromise the model's ability to make accurate predictions, resulting in logic corruption, data manipulation, and data injection. Detecting outliers is a powerful defense against such attacks, helping separate injected elements from the existing data distribution.
Employee theft
The democratization of data access means that every employee holds a level of critical business information, which increases the risk of unintentional or deliberate data leaks. Employee theft is a concern across companies, from startups to tech giants.To counter this threat, companies should implement legal policies and secure networks with virtual private networks. Additionally, Desktop as a Service (DaaS) can restrict data access from local drives, and enhance security.
What are the big data security best practices
In the contemporary data-centric environment, utilizing big data holds substantial promise for enterprises, offering valuable insights and enhanced decision-making capabilities. Nevertheless, it concurrently poses some challenges. Organizations must proficiently sail through and have a well-defined strategy harmonizing technology with their goals. We will explore essential methodologies for ensuring big data security in this context.
Encryption
It assumes a critical role in this endeavor. The imperative is to establish scalable encryption practices encompassing data at rest and data in transit within the comprehensive Big Data pipeline. Scalability takes precedence here as data encryption should extend its protective reach to encompass various analytics tools, their outputs, and storage formats like NoSQL. Encryption's potency emerges from its capacity to render data indecipherable, even when malicious actors intercept data packets or gain access to sensitive files.
User access control
Effective access control is vital to tackling big data security issues like insider threats and excessive privileges. Role-based access management is a valuable method for overseeing access throughout various layers of big data pipelines. For example, data analysts should have access to analytics tools that are not limited to big data developers, like ETL software. Following the principle of least privilege helps restrict access to only the necessary tools and data for a user's tasks.
Cloud security monitoring
Due to the substantial need for storage and processing in big data workloads, cloud computing has become a practical choice for many enterprises. At the same time, vulnerabilities like exposed API keys and misconfigurations in cloud environments can't be ignored. Leaving an AWS data lake on S3 wide open to the internet, for example, is risky. It is easier to mitigate these vulnerabilities when you use an automated scanning tool that quickly checks public cloud assets for security flaws.
Centralized key management
In a complex big data ecosystem, encryption security requires a centralized key management approach to ensure effective and policy-driven handling of encryption keys. Centralized key management also controls key governance from creation to key rotation. For businesses running big data workloads in the cloud, Bring Your Own Key (BYOK) is probably the best option that allows for centralized key management without handing over control of encryption key creation and management to a third-party cloud provider.
Network traffic analysis
Within a big data pipeline, an ongoing stream of data is continuously ingested from various origins, encompassing sources like real-time data from social media platforms and information from user endpoints. The analysis of network traffic serves as a means to gain insight into this traffic and identify any irregularities, such as the presence of potentially harmful data from IoT devices or the utilization of unsecured communication protocols.
Insider threat detection
In the 2021 report, it was revealed that nearly all organizations, 98% to be precise, have concerns about their susceptibility to insider attacks. Within the realm of big data, insider threats pose significant risks to the confidentiality of sensitive corporate information. A malicious insider with access to analytics reports and dashboards might potentially disclose valuable insights to competitors or even attempt to sell their login credentials. To proactively detect insider threats, start with examining logs for common business applications like RDP, VPN, Active Directory, and endpoints. These logs can reveal unusual activities that warrant further investigation, such as unexpected data downloads or irregular login patterns.
Threat hunting
Threat hunting is a proactive effort to uncover hidden threats in your network. Led by an experienced cybersecurity analyst who uses real-world attack data and insights from security tools, its goal is to formulate hypotheses about potential threats. Big data can assist in this process by uncovering concealed insights within large sets of security data. For big data security enhancement, threat hunting involves examining datasets and infrastructure for signs of compromise in your big data environment.
Incident investigation
Monitoring big data security involves collecting vast amounts of data, usually fed into a Security Information and Event Management (SIEM) system. However, SIEM systems can be overwhelmed by the high-speed data generation in big data environments, which results in numerous false alarms and alerts for analysts. Ideally, an incident response tool should provide context for security threats, streamlining and expediting incident investigations.
User behavior analytics
User behavior analytics goes beyond insider threat detection. It continuously monitors user interactions, sets a baseline for normal behaviors and generates alerts for any deviations. This improves the ability to detect insider threats and compromised accounts, enhancing asset security in the big data environment.
Data exfiltration detection
Security leaders worry about unauthorized data transfers in big data pipelines, where vast amounts of sensitive assets can be copied. Detecting data exfiltration requires monitoring outbound traffic, IP addresses, and network activity. Prevention involves tools for code security, misconfiguration checks, data loss prevention, and next-gen firewalls. Educating and raising awareness within your organization is essential.
What companies are top on the big data security market
Digital security is a vast industry with numerous players on the market. In contrast, the realm of big data security is smaller because of its technical complexity and scalability demands. Nevertheless, organizations that manage big data are investing significantly in the security of their valuable assets, and vendors are actively catering to this demand. Here are some notable companies specializing in big data security.
Microsoft Corporation

Microsoft, a global technology corporation, offers a range of software products, including Internet Explorer, Microsoft Windows OS, Microsoft Office Suite, and Edge Web browsers. The company operates across three business segments: productivity and business process, intelligent cloud, and personal computing.
Microsoft provides various big data security solutions, encompassing cloud security, identity and access management, intrusion prevention systems, and information protection solutions.
IBM Corporation

IBM's data security portfolio prioritizes diverse environments, compliance with global data regulations, and user-friendly solutions for post-deployment data source and security management. Key areas of IBM's focus in data security encompass the management of hybrid cloud security, embedded policy and regulations, and secure open-source analytics.
Snowflake

Snowflake's data experts advocate for the native integration of data security into all data management systems, prioritizing it as a core element rather than an add-on. Within Snowflake's Data Cloud, robust data security features such as data masking and end-to-end encryption for data in transit and at rest are seamlessly incorporated. Additionally, users benefit from accessible support, enabling them to submit reports for analysis through Snowflake and their partner, HackerOne, within their private bug program.
McAfee LLC

Established in 1987 and based in California, USA, McAfee is a cutting-edge cybersecurity company. It focuses on delivering advanced security solutions and caters to consumers, small and large businesses, enterprises, and governments. The company offers many solutions and services, including big data security, data loss prevention, mobile security, encryption, web gateway, server security, intrusion prevention systems, identity and access management, and enterprise security services.
Oracle Corporation

Oracle, a major player in the big data arena, not only excels as a database host but also offers robust security tools. Their security offerings encompass security assessment, data protection, access control, and auditing and monitoring. Additionally, Oracle provides platform-specific security support for two flagship solutions: Autonomous Database and Exadata.
Bottom line
To secure a big data platform from threats, a company should pick proven and efficient security tools.
Across all industries, practices, and tools for big data security are continuously evolving. Big data security benefits, easy implementation, and advanced security tools will help companies overcome all of the hurdles.