Analyze with AI
Get AI-powered insights from this Mad Devs article:
In today's rapidly evolving digital landscape, Artificial Intelligence continues to make its mark across various industries, revolutionizing how we live and work. As anticipation builds for AI's transformative impact in numerous sectors, there's one area where its presence has already been firmly established and has become an indispensable component. Integrating AI in cybersecurity is no longer a distant dream but a reality, shaping and fortifying our defenses against the ever-growing and increasingly sophisticated cyber threats looming over the digital world.
This article looks closely at the various types of AI playing a key role in protecting our data. We'll discuss how and where neural networks are employed for security purposes and outline the benefits and limitations of using neural networks in cybersecurity. Additionally, we'll explore the trends AI is shaping soon in cybersecurity. Dive into our article for an informative and engaging read!
What is artificial intelligence?
Artificial Intelligence (AI) is a broad discipline that focuses on creating machines and systems capable of performing tasks that would normally require human intelligence. It encompasses various subfields and technologies, such as rule-based systems, neural networks, and deep neural networks, each with different principles, capabilities, and applications.
Rule-based systems
Think of these as the early pioneers of AI. They rely on a set of predefined rules and algorithms to make decisions, but they're not quite as flexible as their more advanced counterparts. They can handle specific tasks but can't learn or adapt to new situations like other AI technologies.
Neural networks
Inspired by the structure and function of our biological neural networks, these AI models consist of interconnected nodes (or neurons) that process and transmit information. Neural networks are quite versatile, learning patterns and relationships within data through a process called training. They've proven their worth in various applications, from image recognition to Natural Language Processing (NLP).
Deep neural networks
The cutting edge of AI is deep neural networks (DNNs), a more advanced type of neural network boasting multiple hidden layers between the input and output layers. These hidden layers allow DNNs to learn more complex, hierarchical representations of data, making them perfect for tasks requiring higher levels of abstraction, such as computer vision or speech recognition.
What kinds of AI are used for cybersecurity?
Each AI technology brings unique capabilities and strengths, shaping how we approach and tackle cybersecurity challenges. The following section will explore the diverse kinds of AI used in cybersecurity.
Generative neural networks
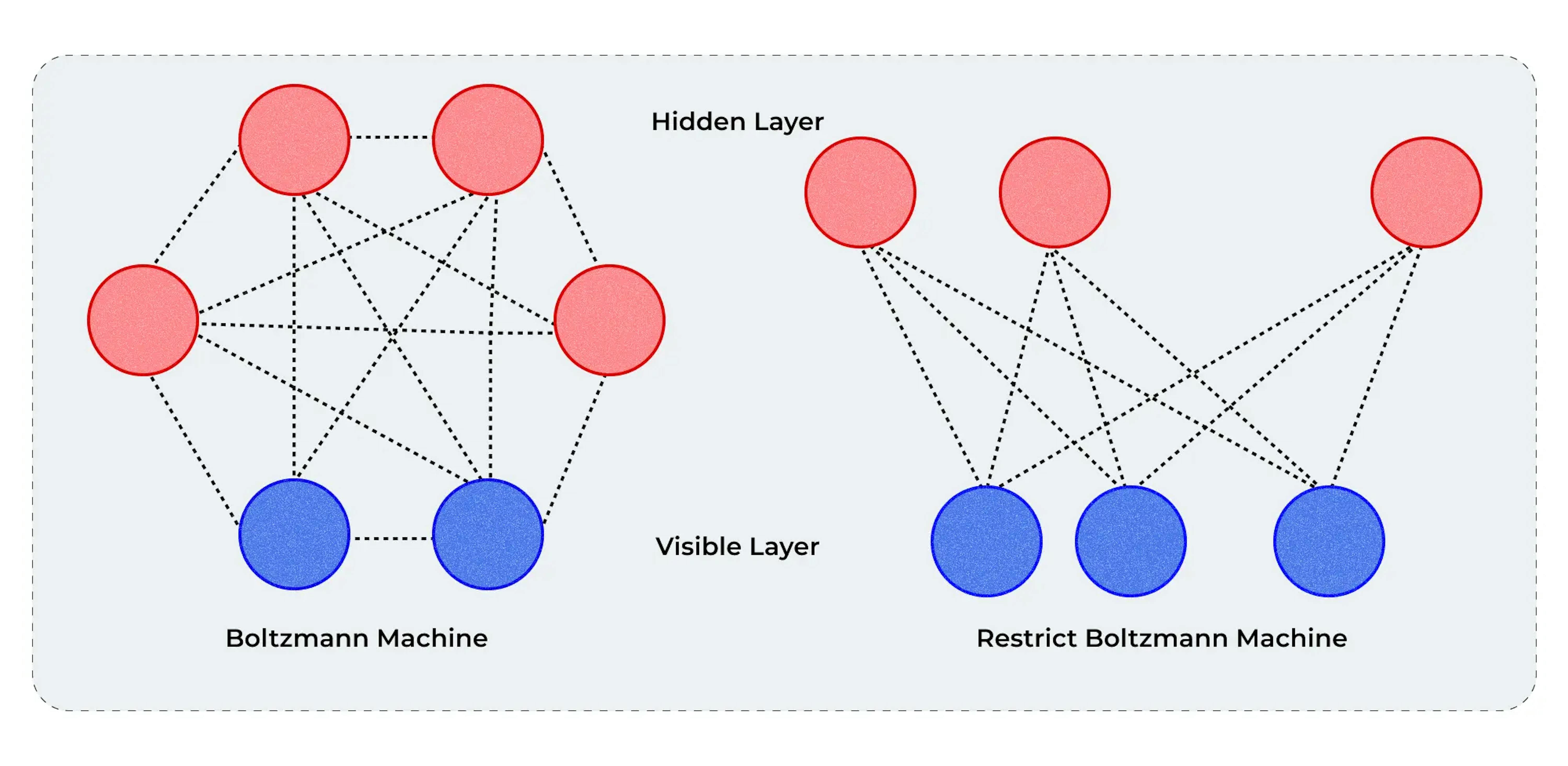
Generative neural networks (GNNs) is a type of artificial neural network that can generate new data points similar to the ones they have been trained on. They are designed to learn the underlying structure of the data, allowing them to produce realistic and diverse samples.
Examples of GNNs include variational autoencoders (VAEs) and restricted Boltzmann machines (RBMs). In cybersecurity, GNNs are primarily used for data augmentation, anomaly detection, and simulating cyberattacks. By generating new data points, they help create robust datasets for training other machine learning models.
GNNs can also identify anomalies in network traffic or user behavior by comparing them to the generated data patterns. Additionally, they can simulate various attack scenarios to test and improve the resilience of cybersecurity systems.
Adversarial neural networks
Adversarial neural networks (ANNs) have several varieties that often become part of other types of neural networks, like GANs. Such examples are adversarial autoencoders (AAEs), a type of autoencoder trained to encode data into a lower-dimensional space while training a discriminator to distinguish between encoded data and random noise.
ANNs refer to training machine learning models to resist adversary attacks. These attacks include creating malicious inputs to trick models into making incorrect predictions or classifications. ANNs are designed to enhance a model's ability to withstand such attacks by incorporating adverse examples into the learning process.
In cybersecurity, ANNs are used to make machine learning models more resilient to adversary attacks. Training models on adverse examples makes them more resilient to such attacks and improves overall security. This approach is particularly useful in pattern recognition, NLP, and intrusion detection systems, where adversary attacks can have significant consequences.
Generative adversarial networks
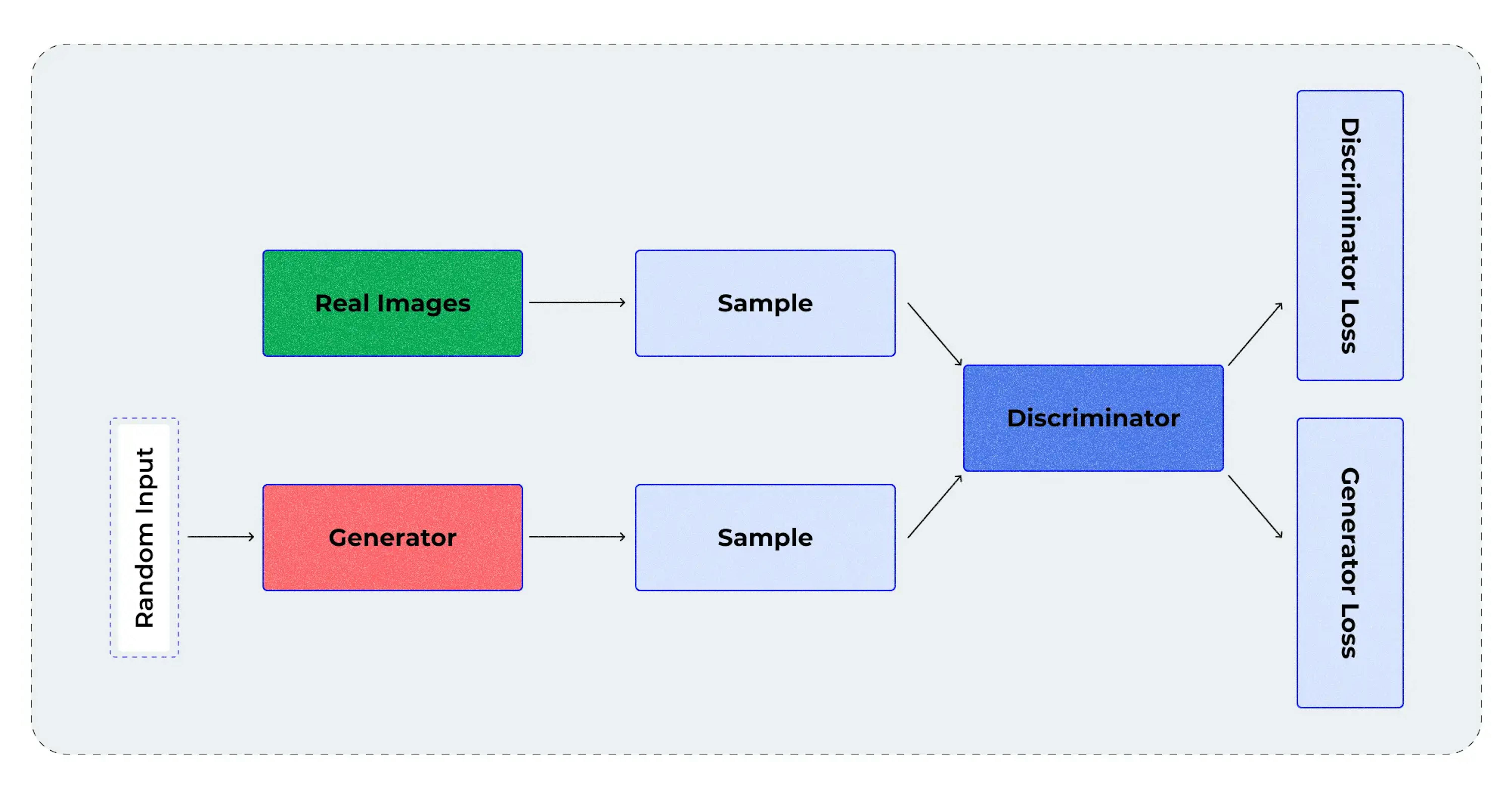
Generative adversarial networks (GANs) are a unique AI architecture composed of two competing neural networks: the generator and the discriminator. The generator creates synthetic data while the discriminator evaluates its authenticity. This competition results in increasingly realistic data generation with various applications.
In cybersecurity, GANs offer several advantages. GANs enable data augmentation, vulnerability discovery, and attack simulation, enhancing overall threat detection and response. GANs provide valuable insights by mimicking cybercriminal behaviors and allow organizations to refine their security approaches.
Recurrent Neural Networks
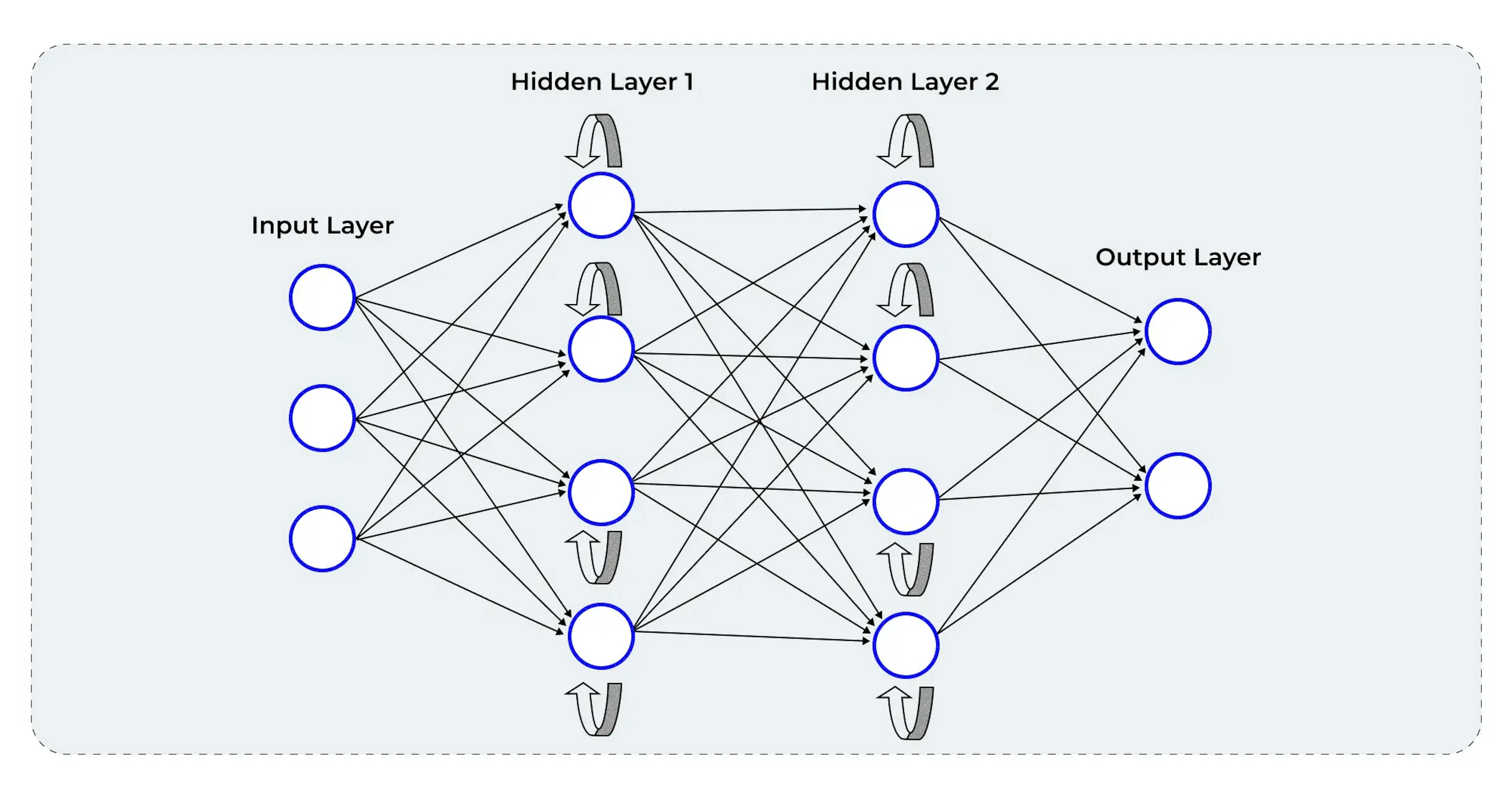
Recurrent neural networks (RNNs) are designed to process sequential data, making them particularly adept at handling time series analysis or NLP tasks.
Their unique architecture allows them to maintain a hidden state, serving as a memory form. This hidden state enables RNNs to remember and use past inputs to predict future events better. RNNs can identify patterns and trends in data streams, helping to detect anomalies and potential intrusions. Their ability to handle sequential data enables them to recognize long-term dependencies, contributing to the early detection of cyber-attacks and proactive threat mitigation.
Convolutional neural networks
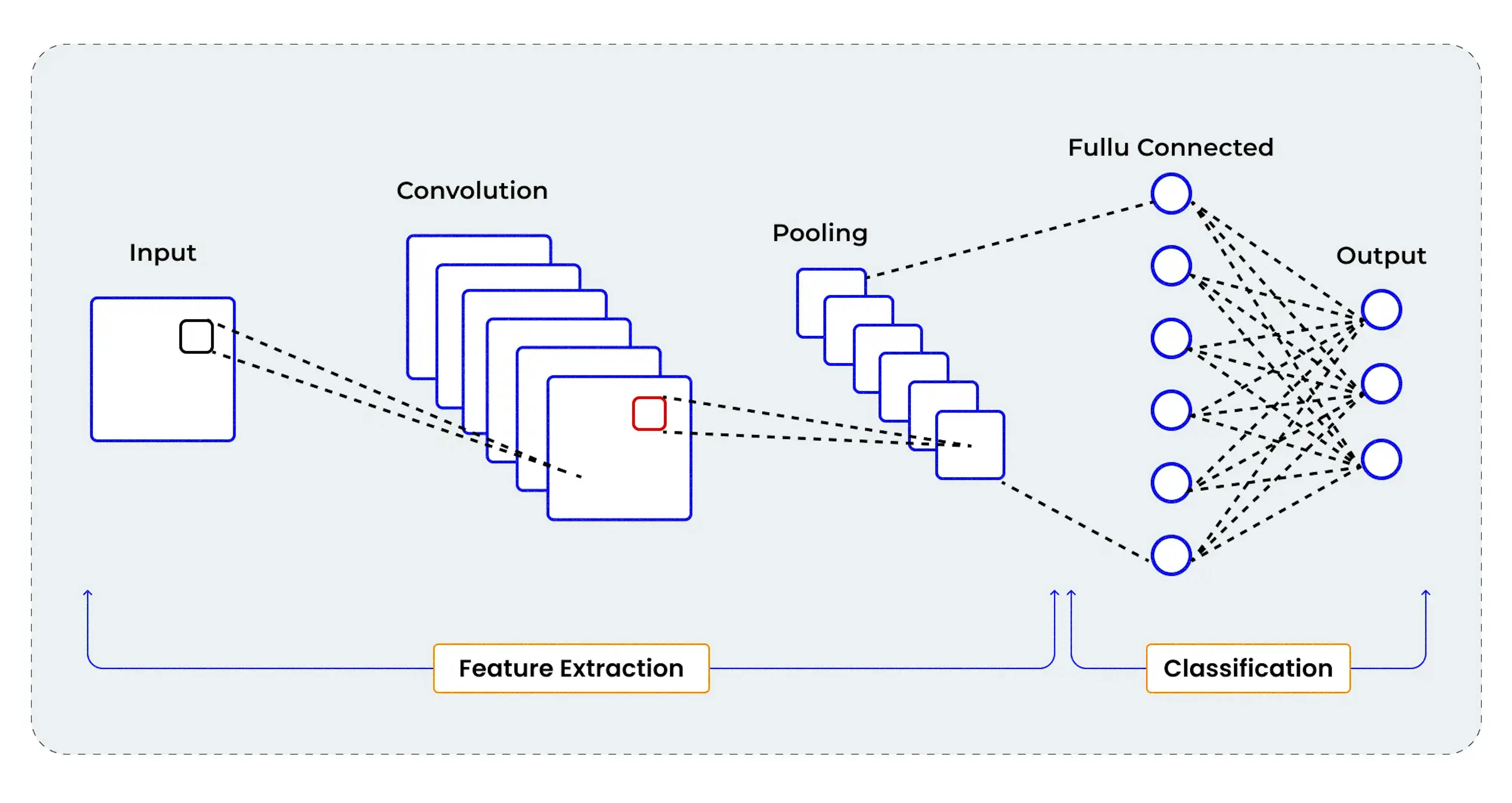
Convolutional neural networks (CNNs) are specialized neural networks designed for image processing and computer vision tasks. They employ a technique called convolution, which involves the application of multiple filters to the input data to identify specific features or patterns. This process allows CNNs to learn hierarchical representations of the input data, making them suitable for tasks that require recognizing complex patterns.
Because CNNs are specialized in pattern recognition and are widely employed in cybersecurity for tasks such as malware and intrusion detection. By analyzing various file formats and identifying distinctive patterns associated with malicious content, CNNs can accurately detect previously unseen threats. Their ability to process large volumes of data in parallel also makes them efficient for real-time threat detection and response.
The use cases of AI in cybersecurity
The distinct strengths of various types of AI are employed in versatile ways to enhance our digital protection. From straightforward solutions utilizing a single type of neural network to more sophisticated systems that integrate multiple neural networks, AI presents an array of precise and potent security tools to tackle diverse challenges. Here we will talk about use cases where these AI-driven technologies are put to work.
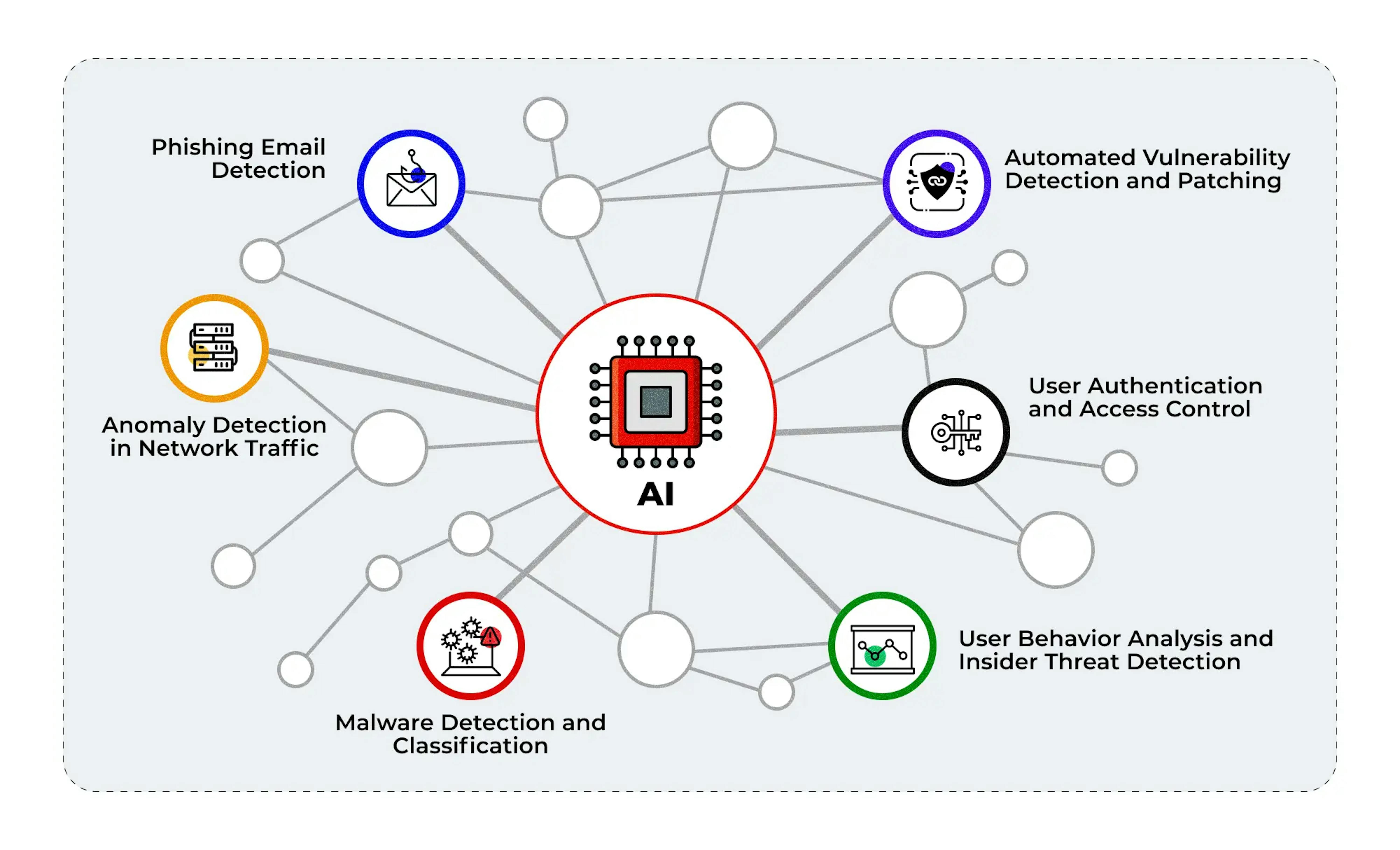
Anomaly detection in network traffic
Anomaly detection in network traffic helps identify malicious activities, intrusions, or unusual behavior patterns. In this use case, RNNs are employed to analyze time-series data, such as network packets or logs, and detect deviations from typical patterns. RNNs are particularly well-suited for this task because they can handle sequential data and retain information about previous states.
RNNs can learn normal patterns and identify anomalies in real-time by processing network traffic data. They can flag potential threats, such as distributed denial of service (DDoS) attacks or data exfiltration attempts, allowing security teams to respond promptly and mitigate risks. RNNs' ability to adapt to evolving traffic patterns ensures they remain effective even as network conditions change or new threats emerge.
Malware detection and classification
Malware detection and classification enable organizations to identify and neutralize malicious software before it can cause harm. CNNs can be employed in this use case to analyze binary files, such as executables or documents, and determine if they contain malware.
Organizations can enhance their security posture by employing CNNs for malware detection and reduce the likelihood of successful attacks or data breaches. CNNs are trained on large datasets of benign and malicious files, learning to identify patterns and features associated with malware. They can then analyze new files and classify them based on their similarity to known malware samples. This approach allows for rapid and accurate detection of malware, even as new variants emerge.
User authentication and access control
User authentication and access control ensure that only authorized individuals can access sensitive data and resources within an organization. Organizations can develop advanced and secure user authentication methods by leveraging a combination of CNNs, RNNs, and GNNs.
CNNs can be employed for biometric authentication, such as facial recognition or fingerprint scanning. These networks can analyze visual data and distinguish between authorized users and intruders. RNNs can analyze user behavior patterns, such as keystroke dynamics or mouse movement, creating a continuous and unobtrusive authentication mechanism. This helps identify unauthorized users even after the initial login by monitoring and evaluating the user's behavior throughout the session. GNNs can be used to model the relationships between users, devices, and resources in a network, allowing for more granular and context-aware access control. By understanding an organization's complex dependencies and interactions, GNNs can help identify unusual access requests or potential security risks, enhancing the overall security posture.
By combining the strengths of CNNs, RNNs, and GNNs, organizations can develop a multi-layered authentication and access control system that provides robust security while reducing the risk of unauthorized access and data breaches.
Phishing email detection
Phishing emails are a common attack vector that tricks users into revealing sensitive information or installing malware on their devices. A combination of RNNs and CNNs can be employed to detect and block phishing emails.
RNNs are useful for analyzing the textual content of emails and looking for patterns and sequences indicative of phishing attempts. They can be trained on large datasets of phishing and legitimate emails to develop a model that can effectively distinguish between them. Meanwhile, CNNs can be employed to analyze the visual aspects of an email, such as embedded images or logos, which are often used in phishing emails to mimic legitimate organizations.
By combining the strengths of RNNs and CNNs, a robust phishing email detection system can be developed that analyzes both textual and visual elements of emails, increasing the accuracy and effectiveness of phishing detection and protection.
User behavior analysis and insider threat detection
User behavior analysis and insider threat detection involve monitoring user activities within an organization to identify suspicious or potentially harmful actions. RNNs and GNNs can work together to model normal user behavior and detect deviations that may indicate an insider threat in this use case.
RNNs analyze the sequence of user actions, such as file access, login attempts, or data transfers, and learn to identify typical behavior patterns. GNNs generate new data points based on the learned patterns, helping to create a more robust understanding of normal user behavior. The system can identify anomalies and flag potential insider threats by comparing real-time user activities to the expected behavior patterns generated by the GNNs.
This approach allows organizations to proactively respond to potential security risks and protect their sensitive data and systems.
Automated vulnerability detection and patching
Automated vulnerability detection and patching involve identifying security flaws in software applications or systems and applying necessary updates to address them. RNNs and CNNs can be combined to analyze both code and configuration files, identifying potential vulnerabilities and suggesting appropriate fixes.
RNNs can be used to process the source code of applications, analyze the sequence of instructions, and detect patterns associated with known vulnerabilities. By learning from large code datasets with known vulnerabilities, RNNs can identify similar issues in new applications and suggest possible fixes. CNNs can be applied to analyze configuration files, identifying misconfigurations or insecure settings that may expose systems to potential attacks.
By automating this process, organizations can reduce the likelihood of successful attacks, maintain a strong security posture, and improve overall system reliability.
Benefits of siung AI in cybersecurity
- Faster detection of underlying vulnerabilities. AI-driven solutions can quickly identify weaknesses in systems, reducing the window of opportunity for cybercriminals to exploit these vulnerabilities. Studies show that AI can reduce the average time to detect vulnerabilities from weeks to mere hours or even minutes.
- Better risk identification and informed security measures. AI-powered analytics enable organizations to gain deeper insights into their security posture and implement targeted data-driven security measures.
- Around-the-clock monitoring and threat mitigation. AI-based cybersecurity tools provide automatic 24/7 monitoring and can significantly decrease the average time to respond to security incidents, enabling organizations to prevent or limit the impact of breaches more effectively.
- Reduced burden on cybersecurity professionals. AI automates routine tasks, freeing up security specialists to focus on more complex challenges.
- Improved efficiency and cost-effectiveness. AI-driven cybersecurity solutions streamline processes, minimize human error, and reduce the reliance on manual labor.
- Enhanced incident response. AI-powered tools can analyze and prioritize security incidents, enabling organizations to respond more quickly and effectively to breaches.
- Scalability and adaptability. AI-based cybersecurity solutions can adapt and scale to meet the evolving needs of businesses, providing a more resilient and agile security infrastructure that can grow alongside the organization.
- Proactive threat hunting. AI-driven solutions can actively search for potential threats within an organization's digital environment, identifying and addressing risks before they escalate into full-blown attacks.
Limitations of using AI in cybersecurity
- AI won't help with the unique threats. AI is typically trained on historical data and patterns. As a result, it might struggle to detect and respond to entirely new or highly sophisticated kinds of threats that have never been seen before.
- AI won't help you find creative ways to attack a system. While AI can identify known vulnerabilities and attack patterns, it may not be effective in discovering novel attack vectors that require out-of-the-box thinking or human ingenuity.
- AI is also a great new tool for cybercriminals. As AI advances in security, it can also be leveraged by malicious actors to create more potent threats, such as developing sophisticated malware or automating attacks at scale. This can escalate the arms race between cybersecurity professionals and cybercriminals.
- Dependence on quality data. The effectiveness of AI-driven cybersecurity solutions relies heavily on the quality and quantity of data used for training. Inaccurate or biased data can lead to false positives or negatives, potentially undermining the system's reliability.
- Privacy and ethical concerns. The extensive data collection and analysis required for AI-driven cybersecurity can raise privacy and ethical concerns, especially when sensitive personal or organizational information is involved.
- Integration and compatibility challenges. Implementing AI-driven solutions within existing cybersecurity infrastructures can be complex, as organizations need to ensure seamless integration and compatibility with their current systems and processes.
Future trends of AI in cybersecurity
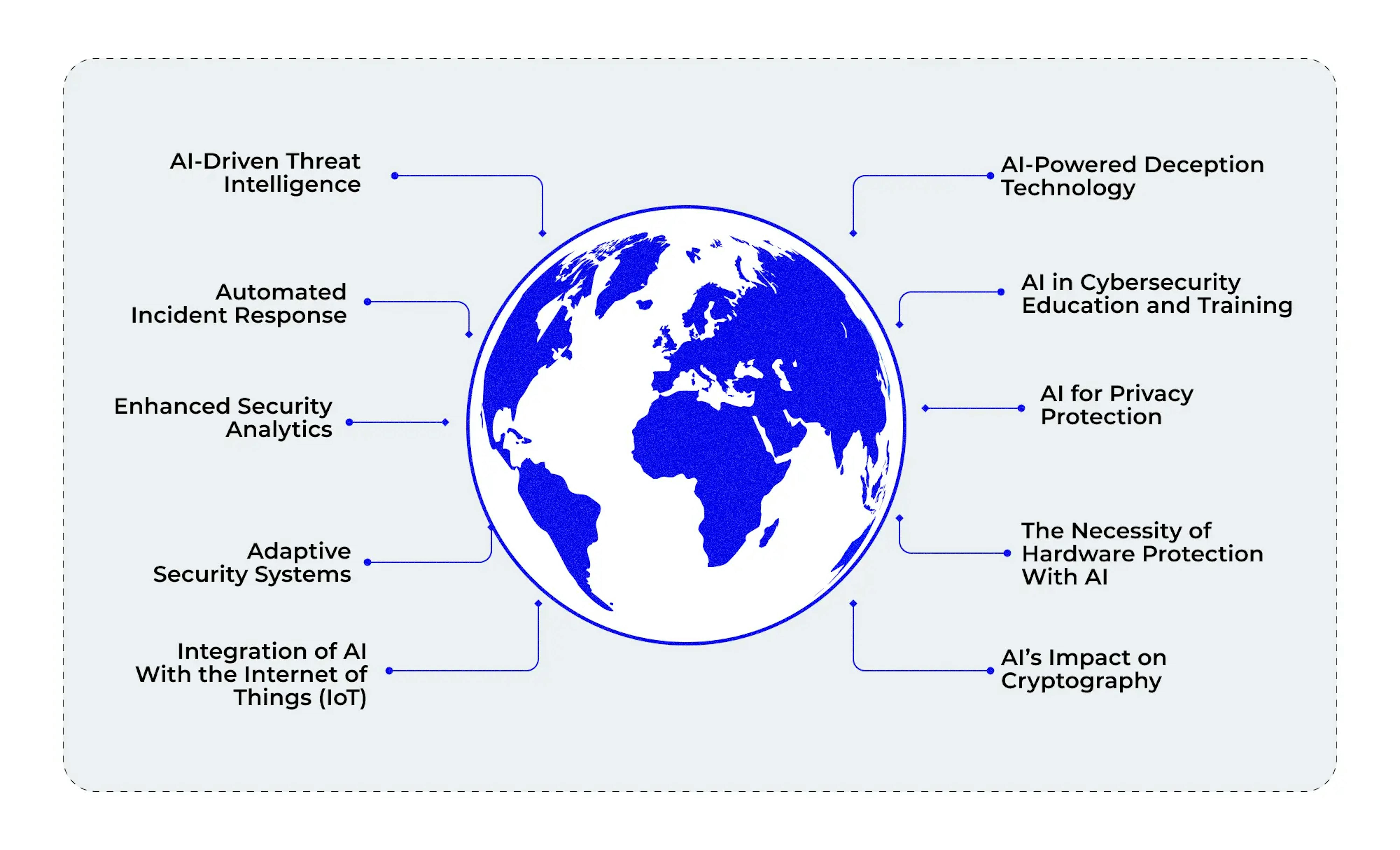
AI-driven threat intelligence
AI algorithms analyze vast amounts of structured and unstructured data from various sources, such as news articles, social media, and dark web forums. By employing NLP and machine learning techniques, AI can identify patterns, trends, and relationships within this data, enabling security teams to predict and prioritize potential threats. As the cyber threat landscape grows more complex, traditional manual methods of threat intelligence will struggle to keep pace, making AI-driven solutions will essential component of modern cybersecurity strategies.
Automated incident response
AI-powered incident response tools use machine learning algorithms to analyze the characteristics of an attack, such as its origin, affected systems, and the type of vulnerability exploited. Based on this analysis, the tool can recommend appropriate remediation measures, initiate containment, and even automate patching or updating affected systems, all in real-time. This automated approach will help organizations respond more quickly and efficiently to security breaches, minimizing potential damage and reducing the time and resources required for recovery.
Enhanced security analytics
AI-driven security analytics solutions employ advanced algorithms to process large datasets, automatically correlating events, detecting potential threats, and providing actionable insights. This enables organizations to proactively identify and address vulnerabilities, reducing the likelihood of successful attacks. As the volume and complexity of security data increase, manual analysis becomes less feasible, making AI-powered analytics a vital tool for extracting meaningful insights and improving overall security posture.
Adaptive security systems
AI-powered cybersecurity systems use machine learning algorithms to learn from previous attacks and continuously adapt their defenses. This ongoing learning and adaptation process will make it more difficult for adversaries to exploit the same vulnerabilities repeatedly. As cyber threats evolve and become more sophisticated, static security measures will be less effective, making adaptive AI-driven solutions essential for maintaining robust defenses.
Integration of AI with the Internet of Things (IoT)
As the number of connected devices continues to grow, so does the attack surface, making AI-powered IoT security increasingly critical. AI-driven security solutions monitor and protect IoT networks by analyzing device behavior and detecting anomalies that may indicate potential attacks. These solutions can learn the normal patterns of device activity and automatically identify deviations, allowing security teams to respond to threats more effectively.
AI-powered deception technology
Using AI in deception technology creates more convincing and dynamic traps, making it harder for attackers to distinguish between real and fake targets. AI algorithms generate realistic decoys and environments that mimic an organization's IT assets. By luring attackers into these false environments, security teams can collect valuable threat intelligence and slow down the progress of an attack.
AI in cybersecurity education and training
Effective training and education will be crucial for maintaining a skilled and knowledgeable workforce as the cyber threat landscape becomes more complex. AI can be used to develop realistic cybersecurity simulations and training environments that help security professionals hone their skills and stay up-to-date with the latest attack techniques. AI-driven training platforms can tailor learning experiences to each individual's style, improving knowledge retention and skill development.
AI for privacy protection
As data privacy regulations become more stringent, AI-powered privacy protection tools will be essential for maintaining compliance and minimizing the risk of data breaches and fines. AI-driven solutions can automate identifying, classifying, and protecting sensitive data, helping organizations ensure compliance with data privacy regulations. By employing machine learning algorithms to analyze and categorize data, AI can streamline the process of data protection and reduce the risk of human error.
The necessity of hardware protection with AI
In today's digital landscape, software protection alone is no longer sufficient to safeguard devices against sophisticated cyber threats. As virtually every device becomes a computer, the risk of hacking increases, making it essential to implement hardware protection even in the smallest devices. This is why hardware security modules (HSMs) have become integral components in laptops and smartphones. By integrating dedicated AI-driven hardware modules, devices will be able to prevent threats more effectively, providing an additional layer of security that goes beyond traditional software-based measures.
AI's impact on cryptography
AI advancements, particularly in neural networks, have significantly improved decryption capabilities. This challenges conventional cryptographic practices, as some encryption methods may become less secure. In response, there will be a growing emphasis on developing new cryptographic techniques and encryption algorithms that are resilient to AI-driven decryption methods. Emerging technologies like post-quantum cryptography and AI-blockchain hybrids may play a key role in shaping the future of secure communication and data protection.
Summary
In conclusion, implementing neural networks as an integral part of cybersecurity has already significantly improved various security systems and solutions. Their active implementation has made these defenses more automated, efficient, and cost-effective.
AI shouldn't be feared as an undeniable presence in the field; rather, it should be continually utilized and enhanced. By embracing AI, we allow human experts to focus on their strengths, such as solving complex problems and making important decisions. As we adapt to this technological landscape, we must recognize the potential for further innovation in cybersecurity, its promise, and its limitations, use it intelligently, and develop it actively.
And if you need help developing or integrating AI-based systems, but are unsure which approach and technology suits your business, contact us for a free one-on-one consultation.












