Analyze with AI
Get AI-powered insights from this Mad Devs article:
Living in a global, super-connected world comes with responsibilities. Cybercrime has become a growing threat, especially in the digital field. With the increasing amount of online transactions and sensitive information, businesses and organizations must assess and mitigate cyberattack risks.
In this article, you will learn cybersecurity risk assessment 101: the main risks businesses face today and how the market reacts to them. Discover the main standards that help you avoid risks in different domains and choose which ones will ensure the safety of your business operation.
What you will learn from the article:
- What are some risks businesses face, including external and internal risks, outdated systems, third-party risks, and software compliance risks?
- What is the market state of cybersecurity assessments with its current capitalization and forecasts?
- What are the main cybersecurity frameworks, like NIST and OWASP, and how do they help to assess and manage cybersecurity risks?
- What are specific industrial standards such as GDPR, HIPAA, PCI DSS, etc., and which additional requirements do they ask for compliance?
- And what are the best risk assessment and managing strategies there?
What risks do businesses face?
When discussing the risks organizations may encounter today, we must delve into a broad spectrum.
External risks
External risks constitute potential threats from the external environment that could harm organizational assets. For example, any activity by malicious actors with the goal to gain unauthorized access to confidential information. This may involve attempts to breach systems, phishing attacks, or other forms of cyberattacks.Internal risks
Internal risks are associated with potential threats from within the organization. These security threats could come from both current and former employees or trusted partners. Such risks include unauthorized access to confidential information, data leaks, or even intentional malicious actions by internal stakeholders.Outdated systems
Outdated systems refer to technological components that are not supported or updated anymore but continue to impact the organization's assets. This may include old computers, servers, software applications, or other obsolete technologies. Such systems can become vulnerabilities through which malicious actors gain access to corporate resources.Third-party risks
Third-party risks emerge when you outsource business processes or functions to third parties, including external suppliers or partners. This process creates a potential risk of intellectual property theft or the leakage of confidential information. Taking measures to assess and manage this risk is critical to ensure data security and confidentiality.Software compliance
This risk is associated with software that does not comply with licensing requirements or is not updated on time. Non-compliance with licensing requirements or the absence of current updates can create system vulnerabilities, which malicious actors may exploit for attacks and data compromise. Managing software compliance becomes a vital component of an information security strategy.
What is the market state of cybersecurity assessments?
Cybercrime is on the rise, and its impact is expanding as technology advances. A recent study by Cybersecurity Ventures predicts that cybercrime will cost the world over $10.5 trillion annually by 2025. It isn’t just the frequency of attacks that is increasing, but also the scope, affecting businesses of all sizes and industries. Despite a slight decline in 2022, the need for effective cybersecurity is more critical than ever for companies looking to protect their assets and maintain their competitive edge.
The consequences of a data leak can be brutal. For example, Marriott International's data breach in 2018 affected over 500 million customers, making it one of the largest data breaches in history, according to the NY Times. As a result of the breach, Marriott faced multiple lawsuits, settlements, and regulatory fines, including a $124 million settlement with the U.K. Information Commissioner's Office, the largest fine ever issued under the General Data Protection Regulation (GDPR) at the time.
The company also faced numerous class-action lawsuits from affected customers and had to pay settlements and legal fees that were estimated to be in the tens of millions of dollars. In addition to these direct costs, Marriott also experienced a decline in its stock value due to the breach. After the announcement of the breach, the company's stock price fell by nearly 10% in the following weeks, wiping out billions of dollars in market value.
Therefore, most businesses got the message and have increased their investment in cybersecurity measures since. In fact, a report by Gartner shows that global spending on cybersecurity is projected to reach $170.4 billion in 2022, with companies of all sizes looking to safeguard against cyber threats. The risks are simply too great to not invest, and the rewards of a secure network far outweigh the costs.
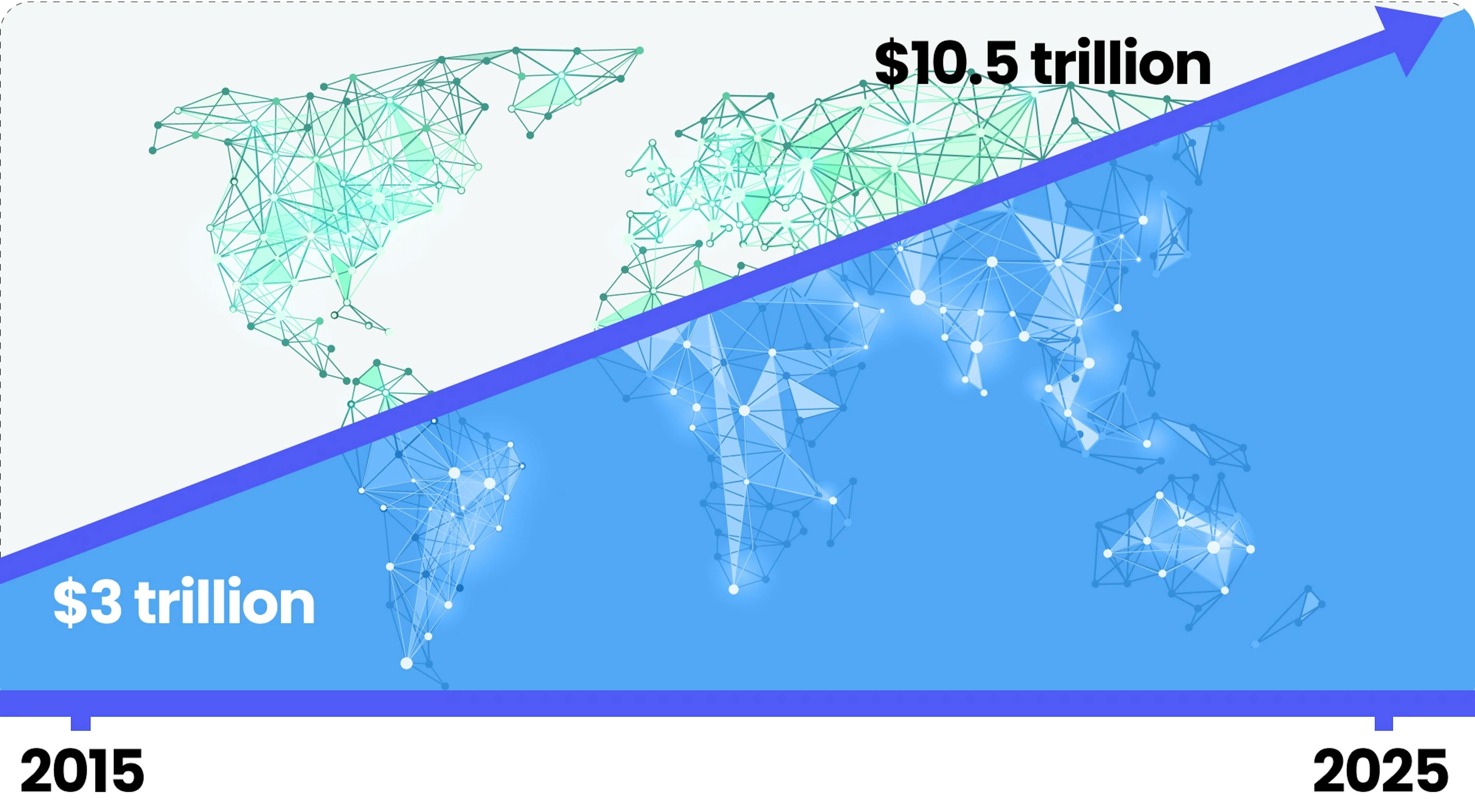
Growth of Cybercrime Costs
Cybersecurity frameworks
Cybersecurity frameworks provide organizations with key standards, guidelines, and practices for managing all risks associated with corporate information and personal data at all levels.
Based on these frameworks, companies can develop robust security policies and build and execute security controls that help them stay safe and compliant with industry standards.
ISO/IEC 27001
ISO/IEC 27001, a globally embraced framework within the ISO 27000 family, empowers organizations of all sizes and industries to safeguard vital assets such as financial data, intellectual property, and employee information. It outlines prerequisites for an effective security management system, offering the best approaches and practices to enhance overall risk management. Notably, while not prescribing specific controls, ISO/IEC 27001 provides a versatile range of tools for organizations to elevate their security posture.
Scope
- Define the boundaries of the Information Security Management System (ISMS).
- Encompass all assets, processes, and risks associated with information security.
Leadership
- Ensure top management commitment to information security.
- Establish an information security policy and define the roles of responsible individuals.
Information security policy
- Develop and approve a documented information security policy.
- Include commitments to continual improvement in the policy.
Risk management
- Identify risks related to information security.
- Assess risks and develop strategies for their management.
Resource management
- Allocate sufficient resources to ensure information security.
- Provide necessary qualifications and awareness for personnel.
Supplier security
- Manage security in the supply chain.
- Assess and manage risks associated with suppliers.
Monitoring, measurement, analysis, and evaluation
- Implement information security monitoring.
- Analyze and evaluate the effectiveness of the Information Security Management System.
Continuous improvement
- Conduct regular reviews and analyses of security measures.
- Take corrective and preventive actions for continual improvement of the system.
The NIST risk management framework (RMF)
Developed by the U.S. National Institute of Standards and Technology (NIST), the framework has quickly gained widespread popularity and has been adopted globally. It establishes fundamental prerequisites for an effective security management system and provides various controls to manage risks and vulnerabilities. NIST RMF provides a structured approach to security and privacy risk assessment and management in 7 distinct steps.
- Prepare. This first step involves activities essential for the pre-emptive management of security and privacy risks.
- Categorize. This entails the development of risk management processes and tasks. Security professionals devise these processes by assessing the impact of risk on the confidentiality, integrity, and availability of systems and information.
- Select. Involves choosing, customizing, and documenting controls that safeguard an organization. This step could include maintaining an updated playbook or assisting in managing documentation to enhance issue resolution efficiency.
- Implement. Focuses on executing security and privacy plans for the organization. Well-constructed plans are vital for minimizing the impact of ongoing security risks.
- Assess. This step includes a check of the established controls and their correct implementation. Organizations strive for operational efficiency, prompting analysts to scrutinize whether implemented protocols, procedures, and controls meet organizational needs.
- Authorize. Authorization involves being accountable for security and privacy risks within an organization.
- Monitor. Monitoring necessitates awareness of how systems operate and ensures that current systems align with the organization's security goals.
The NIST cybersecurity framework (NIST CSF)
NIST CSF focuses on 5 key functions: identification, protection, detection, response, and recovery. They form a strong foundation for cybersecurity risk management, the development of risk management strategies, and past experiences learning.
- Identification. Focuses on the impact of cybersecurity risks on an organization's assets and personnel. For example, the analysis of internal network systems and devices to identify potential security threats.
- Protection. Represents a strategy to ensure organizational security through the implementation of different policies, procedures, training, and tools. It also involves analyzing and enhancing existing policies and procedures to respond to new threats and ensure operational readiness in a changing environment.
- Detection. Aims to identify potential security incidents and improve monitoring capabilities for more effective detection. For instance, to evaluate the settings of new security tools to ensure their effectiveness in risk detection and provide operational alerts to the team about potential threats.
- Response. Helps localize, neutralize, and analyze security incidents through appropriate procedures. For example, to collaborate closely with the team to gather and systematize data, document incidents, and propose process improvements to prevent event recurrence.
- Recovery. Encompasses the process of restoring compromised systems to normal functionality. This includes active participation in collaboration with the team to recover systems, data, and assets, such as financial or legal files, affected by incidents like a breach.
Open Worldwide Application Security Project (OWASP)
Delving further into OWASP security principles, these foundational concepts guide the cybersecurity team in fortifying organizational defenses and mitigating risks.
Minimize attack surface area
- Mitigate potential vulnerabilities (attack surface) exploited by threat actors.
- Some of the examples can include disabling software features and enforcing complex password requirements to thwart common attack vectors like phishing emails.
Principle of least privilege
- Restrict user access to the minimum required for daily tasks.
- Limits the potential damage from a security breach, ensuring compromised credentials provide only restricted access.
Defense in depth
- Employ varied security controls to mitigate risks and threats.
- Examples include multi-factor authentication (MFA), firewalls, intrusion detection systems, and permission settings creating multiple defense layers.
Separation of duties
- Critical actions involve multiple individuals, each adhering to the principle of least privilege.
- Ensures no individual possesses excessive privileges, reducing the risk of system misuse.
Keep security simple
- Avoid unnecessarily complex security solutions.
- Simplification enhances manageability and promotes collaborative work on security controls.
Fix security issues correctly
- Swiftly identify root causes during security incidents, contain impacts, and conduct thorough remediation.
- An example of this is addressing a weak password issue through the implementation of stricter password policies.
Additional OWASP security principles
Establish secure defaults
- The default state of an application should be its optimal security state.
- Users must exert extra effort to compromise security intentionally.
Fail securely
- When a control fails, default to the most secure option.
- Example: A failing firewall should close all connections and block new ones instead of accepting everything.
Don't trust services
- Exercise caution with third-party partners, as their security policies may differ.
- Example: Organizations should verify data accuracy from third-party vendors before sharing it with customers.
Avoid security by obscurity
- Rely on multiple factors for security; don't depend on secrecy.
- Example: Application security shouldn't hinge on keeping source code a secret but should incorporate robust password policies, in-depth defense, network architecture, and fraud controls.
What are the different cybersecurity assessment industrial standards?
Various industries and products have been regulated by specific standards that set the bar for security measures. These standards are in place to protect sensitive information, whether it is personal data, health information, financial data, or even educational records.
GDPR
GDPR (General Data Protection Regulation) is an EU regulation that aims to protect the privacy of EU residents. There are the following requirements and regulations.
Lawful, fair, and transparent processing
- Lawful processing. All processes related to the processing of personal data must have lawful reasoning. Companies can only process data for specific, legally predetermined purposes.
- Fair processing. Companies are responsible for the fairness of data processing. This implies that data is processed solely in consideration of the legal interests of a subject and without using information for unethical purposes.
- Transparent processing. Transparency entails clear and easy-to-understand details about how personal data is processed and used. This includes details about the purposes of processing, storage durations, and any third parties with whom data may be shared.
Limitation of purposes, data, and storage
- Prohibition of processing beyond legal purpose. Companies are obliged to refrain from using personal data beyond the established legal purpose for which the data was collected.
- Duty to collect necessary data only. According to GDPR, companies must limit themselves to collecting only personal data that is strictly necessary to achieve a pre-defined purpose, and requesting excessive or unnecessary data is prohibited.
- Duty to delete data after achieving the purpose. According to GDPR requirements, companies must actively delete personal data after achieving the lawful purpose of its processing, ensuring minimal storage and enhanced data subject privacy.
Rights of data subjects
- Right to information. Data subjects have the right to complete and understandable information about how their personal data is processed, for what purpose, and on what basis.
- Right to access. Data subjects have the right to confirm whether their personal data is being processed, access that data, and obtain information about its processing methods.
- Right to rectification. Data subjects have the right to request the correction of inaccurate or incomplete personal data, ensuring the relevance and accuracy of the information.
- Right to withdraw consent. Data subjects can withdraw their consent for personal data processing at any time if processing is based on consent.
- Right to object. Data subjects have the right to object to processing their personal data if there are legal grounds for such objection.
- Right to object to automated processing. Data subjects can object to decisions based solely on automated processing if such decisions have legal or significant effects.
- Right to be forgotten. Data subjects have the right to request the deletion of their personal data if it is no longer necessary for the purposes for which it was collected.
- Right to data portability. Data subjects can receive their personal data in a structured format and transmit it to other data controllers.
Consent management in compliance
When processing personal data beyond the initially specified lawful purposes, you need to obtain explicit and clear consent from the data subject, who must be at least 16 years old. This consent should be meticulously documented, and the data subject retains the right to revoke it at any time.
Data breach incident management
According to GDPR, organizations must maintain a register of incidents related to personal data breaches. Upon detecting an incident, regulatory authorities and data subjects must be notified within 72 hours, depending on the severity of the breach. GDPR outlines 5 key steps for managing data breaches:
- Notify the data protection officer. Immediate notification to the data protection officer about the identified breach, activation of incident management procedures, and initiation of measures to isolate the breach.
- Assess scale and impact. Thoroughly assess the extent of leaked data, identify potential risks, and evaluate the impact on data subjects and the organization's infrastructure.
- Inform relevant parties. Systematically inform regulatory authorities and data subjects about the nature of the incident, measures taken to prevent harm, and plans for future actions.
- Deep analysis, containment, and notification. Conduct a technical analysis of the breach, implement measures to contain its spread, and notify data subjects if justified by the analysis results.
- Analysis and monitoring. After resolving the breach, conduct a detailed incident analysis to identify root causes and establish monitoring systems to prevent similar incidents in the future.
Integration of privacy in development processes
The principle of privacy requires confidentiality and security aspects to be inherently embedded. When designing new systems and processes, companies must implement organizational and technical protection mechanisms to ensure a high level of data protection from the beginning of the data lifecycle.
Data Protection Impact Assessment (DPIA)
DPIA is a crucial procedure when implementing new projects, changes, or products that involve significant alterations in personal data processing. DPIA involves several key stages:
- Compile data processing list. Provide a detailed description of the data processing process, including usage, controllers, processors, legal basis, and storage periods, aimed at GDPR compliance.
- Evaluate current control measures and risk management. Analyze legal and organizational measures for risk control, encompassing technical and physical aspects, with a focus on GDPR compliance.
- Identify risk sources. Identify threats to confidentiality and reputational risks, including privacy intrusions and potential damage from inaccurate data, considering financial and reputational aspects.
- Analysis and list of negative events and threats. Focus on personal data and assess the impact of new processing, identifying technological threats such as hacking and phishing, with prevention measures for future incidents.
- Report and summary of the analysis. Compile a report with recommendations and action plans to eliminate identified risks, ensuring GDPR compliance and adherence to data processing responsibility principles.
Data transfer
Personal data protection and GDPR compliance are on the controller, even with the third-party processes. Controllers must ensure confidentiality and security during data transfer, adhering to the following principles:
- Responsibility. Active, systematic implementation of appropriate technical and organizational measures.
- Ownership. Integrate technical and organizational measures at all levels of the organization, in each department or function handling personal data processing.
- Documentation. Create relevant documentation to use as evidence of GDPR compliance at any time. Demonstrate compliance to the data protection authorities and stakeholders, including clients and employees.
Data Protection Officer (DPO) appointment
GDPR mandates the appointment of a DPO responsible for advising the company on compliance matters.
Awareness and training
To ensure compliance with GDPR's core requirements, organizations must systematically raise employees' awareness through regular training sessions. These sessions enable employees to understand their data protection responsibilities and identify potential breaches.
HIPAA
HIPAA (Health Insurance Portability and Accountability Act) is a U.S. law that establishes national standards for the confidentiality, privacy, and security of personal health information. It applies to entities involved in healthcare transactions, such as providers and health insurance companies.
Key statements
- Adherence to security rules requires organizations to implement adequate measures to protect electronic media, including administrative, technical, and physical means.
- Insurance organizations are responsible for ensuring the confidentiality, integrity, and availability of electronic PHI.
- The rule implies identifying and protecting against anticipated threats to the security and integrity of information.
- It also supports prohibitions on the unlawful use and disclosure of electronic media, contributing to maintaining the integrity and availability of electronic PHI.
- Insurance companies can flexibly apply the rules, considering their size, complexity, technical infrastructure, security costs, and potential risks for electronic PHI.
Risk analysis and management
- Risk analysis, mandated by security rules, involves assessing the probability and impact of potential threats to electronic PHI.
- Appropriate security measures that mitigate identified risks are a key step in security management.
- Documenting selected security measures and justifying them is necessary for transparency and accountability.
- Maintaining constant, reasonable, and appropriate security protection is an integral part of the risk analysis and management process.
Administrative safeguards
- Security management process. The organization must systematically identify and analyze potential risks to electronic media, taking security measures to reduce them to a reasonable level.
- Security staff. A responsible employee who develops and implements security policies and procedures ensures effective protection management.
- Information access management. Role-based access policies ensure minimal necessary access to electronic PHI, complying with confidentiality standards.
- Training and personnel management. The organization provides resolution and control over employees, regularly training them on security policies and procedures and applying sanctions for violations.
- Policies assessment. The regular assessment of security policies and procedures ensures their compliance with requirements and effectiveness.
Physical safeguards
- Access and object control. Restrict physical access and permit only authorized access to support the organization's security.
- Workstation and device security. Implement policies defining rules for using and accessing workstations and devices to ensure adequate protection of electronic PHI.
Technical safeguards
- Access control. Technical policies and procedures allow only authorized individuals to access electronic PHI.
- Audit control. Access logging and verification mechanisms ensure control over activity in information systems containing electronic PHI.
- Integrity control. Policies and procedures ensure PHI is not altered or destroyed without permission.
- Transmission security. Technical measures protect unauthorized access to transmitted electronic PHI.
PCI DSS
PCI DSS (Payment Card Industry Data Security Standard) is a set of security standards created by major credit card companies to ensure the secure handling of credit card information by companies that accept, process, store, or transmit it.
Firewall installation and maintenance
- Deployment of both hardware and software firewalls.
- Precise configuration of firewall settings, adhering to strict rules.
Implementation of secure configurations and vulnerability management
- Avoidance of default passwords.
- Strengthening systems and applying secure configurations.
- Regular updating of antivirus software.
- Implementation of a vulnerability management program.
Protection of stored account data
- Encryption of stored cardholder data.
- Accurate identification of the location of stored data.
- Creation of a data flow diagram for additional protection.
Data protection during transmission
- Encryption of all transmitted cardholder data.
- Discontinuation of the use of outdated protocols, such as SSL and early TLS.
Protection against malware
- Development of a vulnerability management plan.
- Regular updating of antivirus software.
- Maintenance of up-to-date anti-malware programs.
Development and maintenance of secure systems and software
- Continuous updating of systems and software.
- Application of patches for critical systems.
- Advancement of software development processes.
Limitation of access to system components
- Restriction of access to cardholder data based on business necessity.
- Documentation and implementation of an access control system.
User identification and authentication
- Use of unique identification data for each employee.
- Implementation of multi-factor authentication for additional security.
Physical access limitation
- Control of physical access to workstations.
- Monitoring of POS terminals.
- Conducting regular employee training.
Logging and access tracking
- Implementation of logging and alert systems.
- Configuration of log management.
- Installation of rules for log management.
Regular security testing
- Understanding the environment and conducting quarterly vulnerability scans.
- Performing penetration testing.
Information technology support programs
- Documentation of all processes and security measures.
- Implementation of a risk assessment process.
- Creation of an incident response plan.
CMMC
CMMC (Cybersecurity Maturity Model Certification) is a framework for the cybersecurity of the U.S. Defense Industrial Base. It requires companies to meet various cybersecurity standards depending on the type and sensitivity of the information they handle.
Key points
- Protection of confidential information. Ensure the security of personnel through the safeguarding of confidential information.
- Compliance with DIB standards. Ensure adherence to Defense Industrial Base (DIB) cybersecurity standards for effective resistance to evolving threats.
- Accountability and streamlining. Minimize impediments to comply with Department of Defense requirements and ensure accountability.
- Cybersecurity culture. Reinforce a collaborative culture of cybersecurity and cyber resilience.
- Public trust. Sustain public trust through elevated professional and ethical standards.
CMMC 2.0 security levels
Level 1
- Encompasses 17 requirements.
- Involves annual self-assessment and annual confirmation.
Level 2
- Includes 110 requirements aligned with NIST SP 800-171.
- Requires a three-year assessment by a third-party assessor and annual confirmation.
- Certain programs may undergo a three-year self-assessment and annual confirmation.
Level 3
- Encompasses over 110 requirements based on NIST SP 800-171 and 800-172.
- Requires a three-year assessment by government entities and annual confirmation.
FERPA
FERPA (Family Educational Rights and Privacy Act) is a U.S. law that gives legal guardians the right to inspect and review their children's education records. It also requires schools to protect the confidentiality of student records and limits the release of information without consent.
Key points
This standard is often secondary compared to others and applies to organizations that provide educational services to minors. Usually, adherence to basic administrative, physical, and technical means of ensuring information security, such as GDPR, is also required.
Data сonfidentiality
- Limited access. Schools must ensure limited access to digital educational data. Only authorized individuals with a legitimate educational interest should have access to this information.
- Right to access. FERPA grants parents, legal guardians, and rights holders (students) the right to review and access their digital educational records.
- Data correction. If data is deemed inaccurate or misleading, parents or students have the right to request the correction of digital educational records.
- Consent for disclosure. In most cases, digital educational data cannot be disclosed without written consent from parents or students, except in certain lawful scenarios outlined by FERPA.
Data security
- Security measures. Educational institutions must take security measures to protect digital data from unauthorized access and leaks.
- Staff training. Staff processing digital educational data must be trained and informed about FERPA requirements for properly handling and protecting information.
- Encryption and transmission security. Encryption is required to protect digital data on educational records, especially during transmission over open networks.
Data retention periods
- Compliance with deadlines. Educational institutions must adhere to established deadlines for retaining digital educational data.
However, additional conditions give parents certain privileges regarding their children's educational records. These powers transfer to the students when they reach 18 or continue their education after high school. In such cases, students with these privileges become “rights holders.” Also, the school requires written consent from parents or rights holders to disclose information from educational records. However, according to FERPA, there are exceptions, such as the transfer of information:
- To school employees with a legitimate educational interest;
- To other educational institutions where the student is transferring;
- To specific officials for audit or evaluation purposes;
- To parties providing financial aid to the student;
- To organizations conducting research for the school;
- To accrediting organizations;
- In compliance with a court order or lawfully issued subpoena;
- In emergency situations, to protect health and safety;
- To state and local authorities within the juvenile justice system according to state law.
FINRA
FINRA (Financial Industry Regulatory Authority) is a self-regulatory organization in the United States that oversees and regulates the securities industry. It is responsible for enforcing federal securities laws and regulations and protecting investors by establishing rules and guidelines for the securities industry.
Best interests
- Train staff in best-interests standards.
- Encourage representatives to propose alternatives after recommendations.
- Identify potential conflicts of interest.
- Actively maintain records per requirements.
Cybersecurity
- Encrypt confidential data.
- Address security issues at the branch level.
- Implement robust access controls.
- Ensure supplier compliance with security measures.
- Train staff in cybersecurity threat mitigation.
Public communications
- Retail communication. Any written communication distributed to more than 25 retail investors within 30 days.
- Correspondence. Any written communication distributed to 25 or fewer retail investors within 30 days.
- Institutional communication. Written messages are available only to institutional investors.
All 3 communication categories must be fair and balanced, especially regarding digital assets and managed accounts. FINRA asks for information on investment risks and carefully reviews online communications with clients to assess their status as recommendations. Advertising materials for digital assets must clearly present investment risks and explain the relationship between the broker-dealer and the target investment.
Consolidated Audit Trail (CAT)
Every member company engaged in trading stocks, over-the-counter equity securities, or listed options on the National Market System must report to the Consolidated Audit Trail (CAT). It is important to note that organizations must report all types of proprietary trading activities, including market operations. Unlike some other regulations where the size of the company or its type of trading may affect the eligibility of certain actions, there are no exceptions to the mandatory reporting rule.
Who needs these standards the most?
These standards seem to serve the same purpose and some of the technical requirements they impose overlap. However, let's look at the situations when they are most applicable to business.
GDPR
Companies that want to operate in the European jurisdiction need to take care of GDPR compliance. It is mandatory for anyone working with the user data of European residents, whether it is e-commerce, healthcare, logistics, or any other industry.HIPAA
HIPAA is absolutely mandatory for healthcare operations in the U.S., or if your company plans to offer solutions in this industry to U.S. citizens. In that case, you need to take care of technologies that completely ensure the security and privacy of medical data under this standard.CMMC
For companies in the U.S. defense and government contracting industry, CMMC compliance is also becoming a strategic advantage. This standard emphasizes a high level of cybersecurity in software development, which is essential for working with the government, opening up an entire market not available to most commercial companies targeting the average consumer.FINRA
It is also a mandatory U.S. standard for financial companies that do not just conduct financial transactions but are participants in the stock market. If your company is one of the investment firms, brokerage firms, etc., the reliability of financial systems and compliance with this standard become important factors in attracting customers and investors also wishing to conduct legal financial activities.FERPA
In the U.S. education industry, where student data is processed, FERPA compliance ensures the trust of parents and educational institutions. Suppose your company is in the edtech field and wants to offer online platforms, schools and courses, and other things that non-adults can use for education purposes. In that case, compliance with this standard is essential to enter the U.S. market.
It is important to note that many companies do not adhere to such compliance standards and still operate in these jurisdictions. Many cryptocurrency platforms are a vivid example of how citizens of these countries still favor a company registered outside the jurisdiction of the U.S. or Europe. You can read more about how compliance and non-compliance with regulations limits or benefits companies in our article.
Even though some standards might look redundant for your operations, security compliance always benefits your business. It allows the company to operate fully legally, attract many customers who do not interact with the company due to non-compliance with regulators, and increase the overall level of security by implementing measures to comply with these standards.
Summary
The risks associated with information security are increasing yearly, carrying the potential for great financial or reputational losses. Therefore, dealing with risk assessment, management, minimization, and elimination is a key priority for many businesses. Numerous security frameworks can help with that.
In this article, we covered the types of risks and the standards and regulators that help manage and minimize these risks. This ensures that organizations can continuously conduct business while securing their client data.
If you have any questions or need assistance aligning your company with specific standards, feel free to contact our experts for a free consultation. We are always ready to delve into the intricacies and needs of your business to provide solutions that guarantee seamless operations and the security of corporate and user data.








